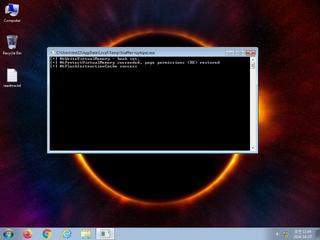
ScreenShot
| Created | 2024.10.27 12:07 | Machine | s1_win7_x6403 |
| Filename | Snaffler-ruylopez.exe | ||
| Type | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 37 detected (Malicious, score, Vr45, confidence, GenericKD, Attribute, HighConfidence, moderate confidence, MalwareX, Kryptik, hzKgty1bItV, AGEN, Static AI, Malicious PE, Detected, Wacatac, Hacktool, 07U0AL, Artemis, Chgt, Edhl) | ||
| md5 | 1af918875c67d204941ec2c8a780e312 | ||
| sha256 | 3621c6a555e79fd6640b3073b245d4e3b225d7a73403e2529d13a82a2b228c7f | ||
| ssdeep | 12288:x/uVxEZsd6Rq8sQ1M7dKHB8u4EqcJDhJzuT6p4qd7DmHrE0S48v7:x/axEadkqbEzTxnp4qdfoE0a | ||
| imphash | e16254f44ddd98c690f5ad4d0a981e4a | ||
| impfuzzy | 24:8fiFlDq+kLEfBlMblR95XG6qKZ86d1TomvlxXUqCvZy:8fiG+k4zslTJG6qA86d1T1vcqC4 | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 37 AntiVirus engines on VirusTotal as malicious |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | Yara rule detected in process memory |
Rules (16cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | Code_injection | Code injection with CreateRemoteThread in a remote process | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|