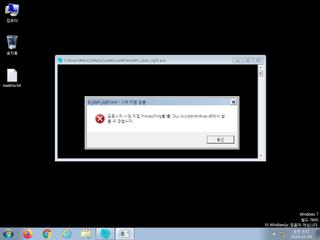
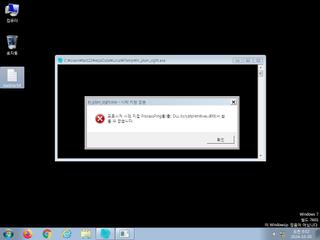
ScreenShot
| Created | 2024.10.30 08:03 | Machine | s1_win7_x6401 |
| Filename | in_plain_sight | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | ddab0e61485ac6c86835861db972fc08 | ||
| sha256 | aaf6846a4346e462cffac18377a79633a0b64498ae5bcbda90b4079354adfa88 | ||
| ssdeep | 49152:gnGtlqkIU6iCVwASOqEDPO/uU9lz7/1Eh6y73Mhg3xdppHo6ww2FVksloB7SXuzR:G+rEd+UkM/ppqdWsllXPoxM/l | ||
| imphash | 5a5b2407af752e729eb125566e218e2d | ||
| impfuzzy | 96:J0NbigxJMnoXPmW5WOmpfRnfc+Zguj9LlNgY6mDz3sw1V:JWt/mW5WLp5x/OY3sw1V | ||
Network IP location
Signature (2cnts)
| Level | Description |
|---|---|
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | This executable has a PDB path |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
kernel32.dll
0x140351750 GetModuleHandleA
0x140351758 GetProcAddress
0x140351760 WaitForSingleObject
0x140351768 GetExitCodeThread
0x140351770 CloseHandle
cryptprimitives.dll
0x140351740 ProcessPrng
api-ms-win-core-synch-l1-2-0.dll
0x140351488 WakeByAddressAll
0x140351490 WakeByAddressSingle
0x140351498 WaitOnAddress
ADVAPI32.dll
0x140351000 CryptGenRandom
0x140351008 RegisterEventSourceW
0x140351010 ReportEventW
0x140351018 CryptAcquireContextW
0x140351020 CryptReleaseContext
0x140351028 DeregisterEventSource
USER32.dll
0x140351320 GetUserObjectInformationW
0x140351328 MessageBoxW
0x140351330 GetProcessWindowStation
CRYPT32.dll
0x140351038 CertFindCertificateInStore
0x140351040 CertFreeCertificateContext
0x140351048 CertOpenSystemStoreW
0x140351050 CertCloseStore
WS2_32.dll
0x1403513a8 getservbyname
0x1403513b0 getservbyport
0x1403513b8 gethostbyaddr
0x1403513c0 inet_ntoa
0x1403513c8 inet_addr
0x1403513d0 htons
0x1403513d8 htonl
0x1403513e0 WSAGetLastError
0x1403513e8 recv
0x1403513f0 gethostbyname
0x1403513f8 select
0x140351400 ntohs
0x140351408 getsockopt
0x140351410 getsockname
0x140351418 ioctlsocket
0x140351420 WSASetLastError
0x140351428 send
0x140351430 getpeername
0x140351438 recvfrom
0x140351440 sendto
0x140351448 setsockopt
0x140351450 closesocket
0x140351458 connect
0x140351460 socket
0x140351468 shutdown
0x140351470 WSAStartup
0x140351478 WSACleanup
KERNEL32.dll
0x140351060 GetFullPathNameW
0x140351068 CreateFileW
0x140351070 CreateThread
0x140351078 CreateNamedPipeW
0x140351080 GetSystemDirectoryW
0x140351088 GetWindowsDirectoryW
0x140351090 GetModuleFileNameW
0x140351098 UnhandledExceptionFilter
0x1403510a0 HeapReAlloc
0x1403510a8 HeapFree
0x1403510b0 SetUnhandledExceptionFilter
0x1403510b8 IsProcessorFeaturePresent
0x1403510c0 InitializeSListHead
0x1403510c8 DuplicateHandle
0x1403510d0 RtlLookupFunctionEntry
0x1403510d8 RtlCaptureContext
0x1403510e0 SetFileInformationByHandle
0x1403510e8 UpdateProcThreadAttribute
0x1403510f0 InitializeProcThreadAttributeList
0x1403510f8 GetExitCodeProcess
0x140351100 TerminateProcess
0x140351108 GetFileAttributesW
0x140351110 CreateProcessW
0x140351118 CompareStringOrdinal
0x140351120 GetEnvironmentStringsW
0x140351128 DeleteProcThreadAttributeList
0x140351130 FreeEnvironmentStringsW
0x140351138 HeapAlloc
0x140351140 GetProcessHeap
0x140351148 GetCurrentThread
0x140351150 SetThreadStackGuarantee
0x140351158 AddVectoredExceptionHandler
0x140351160 IsDebuggerPresent
0x140351168 ReadFileEx
0x140351170 SleepEx
0x140351178 WriteFileEx
0x140351180 GetLastError
0x140351188 SetLastError
0x140351190 RtlVirtualUnwind
0x140351198 GetStdHandle
0x1403511a0 GetFileType
0x1403511a8 WriteFile
0x1403511b0 GetModuleHandleW
0x1403511b8 MultiByteToWideChar
0x1403511c0 InitializeSRWLock
0x1403511c8 ReleaseSRWLockExclusive
0x1403511d0 ReleaseSRWLockShared
0x1403511d8 AcquireSRWLockExclusive
0x1403511e0 AcquireSRWLockShared
0x1403511e8 GetCurrentThreadId
0x1403511f0 TlsAlloc
0x1403511f8 TlsGetValue
0x140351200 TlsSetValue
0x140351208 TlsFree
0x140351210 GetSystemDirectoryA
0x140351218 FreeLibrary
0x140351220 LoadLibraryA
0x140351228 FormatMessageA
0x140351230 VirtualFree
0x140351238 GetEnvironmentVariableW
0x140351240 WideCharToMultiByte
0x140351248 GetACP
0x140351250 FindClose
0x140351258 FindFirstFileW
0x140351260 FindNextFileW
0x140351268 GetCurrentProcessId
0x140351270 GetSystemTimeAsFileTime
0x140351278 SwitchToFiber
0x140351280 DeleteFiber
0x140351288 CreateFiberEx
0x140351290 GetSystemTime
0x140351298 SystemTimeToFileTime
0x1403512a0 InitializeCriticalSection
0x1403512a8 EnterCriticalSection
0x1403512b0 LeaveCriticalSection
0x1403512b8 DeleteCriticalSection
0x1403512c0 ReleaseSemaphore
0x1403512c8 CreateSemaphoreA
0x1403512d0 ConvertFiberToThread
0x1403512d8 ConvertThreadToFiberEx
0x1403512e0 GetConsoleMode
0x1403512e8 SetConsoleMode
0x1403512f0 ReadConsoleA
0x1403512f8 ReadConsoleW
0x140351300 GetCurrentProcess
0x140351308 WriteConsoleW
0x140351310 QueryPerformanceCounter
ntdll.dll
0x140351780 NtWriteFile
0x140351788 RtlNtStatusToDosError
0x140351790 NtReadFile
VCRUNTIME140.dll
0x140351340 memcmp
0x140351348 memset
0x140351350 memmove
0x140351358 strchr
0x140351360 memchr
0x140351368 wcsstr
0x140351370 strrchr
0x140351378 strstr
0x140351380 __C_specific_handler
0x140351388 __current_exception
0x140351390 __current_exception_context
0x140351398 memcpy
api-ms-win-crt-string-l1-1-0.dll
0x1403516b8 strncpy
0x1403516c0 strcspn
0x1403516c8 isspace
0x1403516d0 strspn
0x1403516d8 strncmp
0x1403516e0 strncpy_s
0x1403516e8 strcat_s
0x1403516f0 strcpy_s
0x1403516f8 tolower
0x140351700 isdigit
0x140351708 strcmp
api-ms-win-crt-time-l1-1-0.dll
0x140351718 _time64
0x140351720 _gmtime64_s
api-ms-win-crt-stdio-l1-1-0.dll
0x1403515f8 __p__commode
0x140351600 __stdio_common_vsprintf
0x140351608 _set_fmode
0x140351610 fputs
0x140351618 fopen
0x140351620 __stdio_common_vsscanf
0x140351628 _wfopen
0x140351630 __stdio_common_vsprintf_s
0x140351638 __stdio_common_vfprintf
0x140351640 fclose
0x140351648 feof
0x140351650 ferror
0x140351658 fflush
0x140351660 fgets
0x140351668 _fileno
0x140351670 fread
0x140351678 fseek
0x140351680 ftell
0x140351688 setvbuf
0x140351690 _setmode
0x140351698 __acrt_iob_func
0x1403516a0 fwrite
0x1403516a8 __stdio_common_vswprintf
api-ms-win-crt-heap-l1-1-0.dll
0x1403514e8 calloc
0x1403514f0 realloc
0x1403514f8 malloc
0x140351500 _set_new_mode
0x140351508 free
api-ms-win-crt-utility-l1-1-0.dll
0x140351730 qsort
api-ms-win-crt-runtime-l1-1-0.dll
0x140351538 terminate
0x140351540 _beginthreadex
0x140351548 _crt_atexit
0x140351550 _initterm_e
0x140351558 exit
0x140351560 signal
0x140351568 _initterm
0x140351570 _get_initial_narrow_environment
0x140351578 _initialize_narrow_environment
0x140351580 __p___argc
0x140351588 __p___argv
0x140351590 _register_onexit_function
0x140351598 _cexit
0x1403515a0 _c_exit
0x1403515a8 _configure_narrow_argv
0x1403515b0 _errno
0x1403515b8 _register_thread_local_exe_atexit_callback
0x1403515c0 _seh_filter_exe
0x1403515c8 _set_app_type
0x1403515d0 _initialize_onexit_table
0x1403515d8 strerror_s
0x1403515e0 _exit
0x1403515e8 raise
api-ms-win-crt-filesystem-l1-1-0.dll
0x1403514d8 _stat64i32
api-ms-win-crt-convert-l1-1-0.dll
0x1403514a8 strtoul
0x1403514b0 strtol
0x1403514b8 atoi
api-ms-win-crt-environment-l1-1-0.dll
0x1403514c8 getenv
api-ms-win-crt-math-l1-1-0.dll
0x140351528 __setusermatherr
api-ms-win-crt-locale-l1-1-0.dll
0x140351518 _configthreadlocale
EAT(Export Address Table) is none
kernel32.dll
0x140351750 GetModuleHandleA
0x140351758 GetProcAddress
0x140351760 WaitForSingleObject
0x140351768 GetExitCodeThread
0x140351770 CloseHandle
cryptprimitives.dll
0x140351740 ProcessPrng
api-ms-win-core-synch-l1-2-0.dll
0x140351488 WakeByAddressAll
0x140351490 WakeByAddressSingle
0x140351498 WaitOnAddress
ADVAPI32.dll
0x140351000 CryptGenRandom
0x140351008 RegisterEventSourceW
0x140351010 ReportEventW
0x140351018 CryptAcquireContextW
0x140351020 CryptReleaseContext
0x140351028 DeregisterEventSource
USER32.dll
0x140351320 GetUserObjectInformationW
0x140351328 MessageBoxW
0x140351330 GetProcessWindowStation
CRYPT32.dll
0x140351038 CertFindCertificateInStore
0x140351040 CertFreeCertificateContext
0x140351048 CertOpenSystemStoreW
0x140351050 CertCloseStore
WS2_32.dll
0x1403513a8 getservbyname
0x1403513b0 getservbyport
0x1403513b8 gethostbyaddr
0x1403513c0 inet_ntoa
0x1403513c8 inet_addr
0x1403513d0 htons
0x1403513d8 htonl
0x1403513e0 WSAGetLastError
0x1403513e8 recv
0x1403513f0 gethostbyname
0x1403513f8 select
0x140351400 ntohs
0x140351408 getsockopt
0x140351410 getsockname
0x140351418 ioctlsocket
0x140351420 WSASetLastError
0x140351428 send
0x140351430 getpeername
0x140351438 recvfrom
0x140351440 sendto
0x140351448 setsockopt
0x140351450 closesocket
0x140351458 connect
0x140351460 socket
0x140351468 shutdown
0x140351470 WSAStartup
0x140351478 WSACleanup
KERNEL32.dll
0x140351060 GetFullPathNameW
0x140351068 CreateFileW
0x140351070 CreateThread
0x140351078 CreateNamedPipeW
0x140351080 GetSystemDirectoryW
0x140351088 GetWindowsDirectoryW
0x140351090 GetModuleFileNameW
0x140351098 UnhandledExceptionFilter
0x1403510a0 HeapReAlloc
0x1403510a8 HeapFree
0x1403510b0 SetUnhandledExceptionFilter
0x1403510b8 IsProcessorFeaturePresent
0x1403510c0 InitializeSListHead
0x1403510c8 DuplicateHandle
0x1403510d0 RtlLookupFunctionEntry
0x1403510d8 RtlCaptureContext
0x1403510e0 SetFileInformationByHandle
0x1403510e8 UpdateProcThreadAttribute
0x1403510f0 InitializeProcThreadAttributeList
0x1403510f8 GetExitCodeProcess
0x140351100 TerminateProcess
0x140351108 GetFileAttributesW
0x140351110 CreateProcessW
0x140351118 CompareStringOrdinal
0x140351120 GetEnvironmentStringsW
0x140351128 DeleteProcThreadAttributeList
0x140351130 FreeEnvironmentStringsW
0x140351138 HeapAlloc
0x140351140 GetProcessHeap
0x140351148 GetCurrentThread
0x140351150 SetThreadStackGuarantee
0x140351158 AddVectoredExceptionHandler
0x140351160 IsDebuggerPresent
0x140351168 ReadFileEx
0x140351170 SleepEx
0x140351178 WriteFileEx
0x140351180 GetLastError
0x140351188 SetLastError
0x140351190 RtlVirtualUnwind
0x140351198 GetStdHandle
0x1403511a0 GetFileType
0x1403511a8 WriteFile
0x1403511b0 GetModuleHandleW
0x1403511b8 MultiByteToWideChar
0x1403511c0 InitializeSRWLock
0x1403511c8 ReleaseSRWLockExclusive
0x1403511d0 ReleaseSRWLockShared
0x1403511d8 AcquireSRWLockExclusive
0x1403511e0 AcquireSRWLockShared
0x1403511e8 GetCurrentThreadId
0x1403511f0 TlsAlloc
0x1403511f8 TlsGetValue
0x140351200 TlsSetValue
0x140351208 TlsFree
0x140351210 GetSystemDirectoryA
0x140351218 FreeLibrary
0x140351220 LoadLibraryA
0x140351228 FormatMessageA
0x140351230 VirtualFree
0x140351238 GetEnvironmentVariableW
0x140351240 WideCharToMultiByte
0x140351248 GetACP
0x140351250 FindClose
0x140351258 FindFirstFileW
0x140351260 FindNextFileW
0x140351268 GetCurrentProcessId
0x140351270 GetSystemTimeAsFileTime
0x140351278 SwitchToFiber
0x140351280 DeleteFiber
0x140351288 CreateFiberEx
0x140351290 GetSystemTime
0x140351298 SystemTimeToFileTime
0x1403512a0 InitializeCriticalSection
0x1403512a8 EnterCriticalSection
0x1403512b0 LeaveCriticalSection
0x1403512b8 DeleteCriticalSection
0x1403512c0 ReleaseSemaphore
0x1403512c8 CreateSemaphoreA
0x1403512d0 ConvertFiberToThread
0x1403512d8 ConvertThreadToFiberEx
0x1403512e0 GetConsoleMode
0x1403512e8 SetConsoleMode
0x1403512f0 ReadConsoleA
0x1403512f8 ReadConsoleW
0x140351300 GetCurrentProcess
0x140351308 WriteConsoleW
0x140351310 QueryPerformanceCounter
ntdll.dll
0x140351780 NtWriteFile
0x140351788 RtlNtStatusToDosError
0x140351790 NtReadFile
VCRUNTIME140.dll
0x140351340 memcmp
0x140351348 memset
0x140351350 memmove
0x140351358 strchr
0x140351360 memchr
0x140351368 wcsstr
0x140351370 strrchr
0x140351378 strstr
0x140351380 __C_specific_handler
0x140351388 __current_exception
0x140351390 __current_exception_context
0x140351398 memcpy
api-ms-win-crt-string-l1-1-0.dll
0x1403516b8 strncpy
0x1403516c0 strcspn
0x1403516c8 isspace
0x1403516d0 strspn
0x1403516d8 strncmp
0x1403516e0 strncpy_s
0x1403516e8 strcat_s
0x1403516f0 strcpy_s
0x1403516f8 tolower
0x140351700 isdigit
0x140351708 strcmp
api-ms-win-crt-time-l1-1-0.dll
0x140351718 _time64
0x140351720 _gmtime64_s
api-ms-win-crt-stdio-l1-1-0.dll
0x1403515f8 __p__commode
0x140351600 __stdio_common_vsprintf
0x140351608 _set_fmode
0x140351610 fputs
0x140351618 fopen
0x140351620 __stdio_common_vsscanf
0x140351628 _wfopen
0x140351630 __stdio_common_vsprintf_s
0x140351638 __stdio_common_vfprintf
0x140351640 fclose
0x140351648 feof
0x140351650 ferror
0x140351658 fflush
0x140351660 fgets
0x140351668 _fileno
0x140351670 fread
0x140351678 fseek
0x140351680 ftell
0x140351688 setvbuf
0x140351690 _setmode
0x140351698 __acrt_iob_func
0x1403516a0 fwrite
0x1403516a8 __stdio_common_vswprintf
api-ms-win-crt-heap-l1-1-0.dll
0x1403514e8 calloc
0x1403514f0 realloc
0x1403514f8 malloc
0x140351500 _set_new_mode
0x140351508 free
api-ms-win-crt-utility-l1-1-0.dll
0x140351730 qsort
api-ms-win-crt-runtime-l1-1-0.dll
0x140351538 terminate
0x140351540 _beginthreadex
0x140351548 _crt_atexit
0x140351550 _initterm_e
0x140351558 exit
0x140351560 signal
0x140351568 _initterm
0x140351570 _get_initial_narrow_environment
0x140351578 _initialize_narrow_environment
0x140351580 __p___argc
0x140351588 __p___argv
0x140351590 _register_onexit_function
0x140351598 _cexit
0x1403515a0 _c_exit
0x1403515a8 _configure_narrow_argv
0x1403515b0 _errno
0x1403515b8 _register_thread_local_exe_atexit_callback
0x1403515c0 _seh_filter_exe
0x1403515c8 _set_app_type
0x1403515d0 _initialize_onexit_table
0x1403515d8 strerror_s
0x1403515e0 _exit
0x1403515e8 raise
api-ms-win-crt-filesystem-l1-1-0.dll
0x1403514d8 _stat64i32
api-ms-win-crt-convert-l1-1-0.dll
0x1403514a8 strtoul
0x1403514b0 strtol
0x1403514b8 atoi
api-ms-win-crt-environment-l1-1-0.dll
0x1403514c8 getenv
api-ms-win-crt-math-l1-1-0.dll
0x140351528 __setusermatherr
api-ms-win-crt-locale-l1-1-0.dll
0x140351518 _configthreadlocale
EAT(Export Address Table) is none