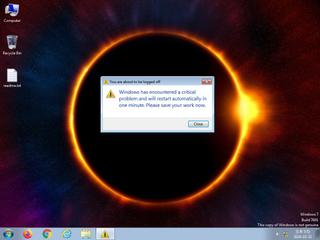
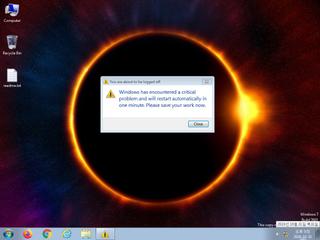
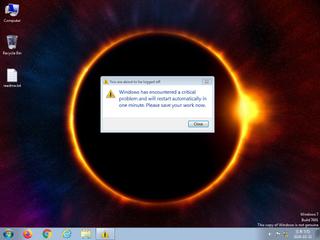
ScreenShot
| Created | 2024.10.31 18:09 | Machine | s1_win7_x6403 |
| Filename | minecraft.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 42 detected (AIDetectMalware, Malicious, score, GenericKD, Unsafe, confidence, CHMP, Attribute, HighConfidence, moderate confidence, KillProc2, Real Protect, PowerShell, Alien, Detected, Phonzy, Malware@#36w60dwm4dpfh, Bankinc, Eldorado, R426832, Artemis, Chgt, susgen) | ||
| md5 | 09718d571b01cb93e6f983be7b99a4b2 | ||
| sha256 | 6eb25168bde4a9e7f3a273229ca0fbf4f17133788b5c68bf3151eb48826e1169 | ||
| ssdeep | 1536:34dJooh0Wa0aer344Jw/ytUqVS5EkIijQ1fTNiPJ:34dzVTaer344JzthRZijQ1Ji | ||
| imphash | a50e815adb2cfe3e58d388c791946db8 | ||
| impfuzzy | 6:dOcid4EZBJAEoZ/OEGDzyRkdc9WNsYb7D4QHDcTxsL4Bn:dC4EBABZG/DzZ4QYTxs0B | ||
Network IP location
Signature (17cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 42 AntiVirus engines on VirusTotal as malicious |
| watch | Deletes a large number of files from the system indicative of ransomware |
| watch | Deletes executed files from disk |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| watch | Uses suspicious command line tools or Windows utilities |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a suspicious process |
| notice | Creates executable files on the filesystem |
| notice | Executes one or more WMI queries |
| notice | Terminates another process |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is compressed using UPX |
| notice | Uses Windows utilities for basic Windows functionality |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Command line console output was observed |
| info | Queries for the computername |
Rules (24cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Gen_1_0904B0_Zero | Win32 Trojan Emotet | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerException__SetConsoleCtrl | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | ftp_command | ftp command | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
COMCTL32.DLL
0x140026588 InitCommonControlsEx
GDI32.DLL
0x140026598 GetStockObject
KERNEL32.DLL
0x1400265a8 LoadLibraryA
0x1400265b0 ExitProcess
0x1400265b8 GetProcAddress
0x1400265c0 VirtualProtect
msvcrt.dll
0x1400265d0 free
OLE32.DLL
0x1400265e0 CoInitialize
SHELL32.DLL
0x1400265f0 ShellExecuteExW
SHLWAPI.DLL
0x140026600 PathRemoveArgsW
USER32.DLL
0x140026610 SetFocus
WINMM.DLL
0x140026620 timeBeginPeriod
EAT(Export Address Table) is none
COMCTL32.DLL
0x140026588 InitCommonControlsEx
GDI32.DLL
0x140026598 GetStockObject
KERNEL32.DLL
0x1400265a8 LoadLibraryA
0x1400265b0 ExitProcess
0x1400265b8 GetProcAddress
0x1400265c0 VirtualProtect
msvcrt.dll
0x1400265d0 free
OLE32.DLL
0x1400265e0 CoInitialize
SHELL32.DLL
0x1400265f0 ShellExecuteExW
SHLWAPI.DLL
0x140026600 PathRemoveArgsW
USER32.DLL
0x140026610 SetFocus
WINMM.DLL
0x140026620 timeBeginPeriod
EAT(Export Address Table) is none