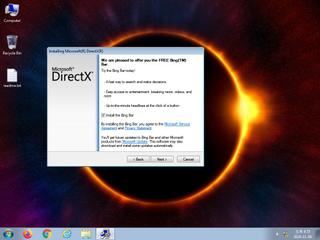
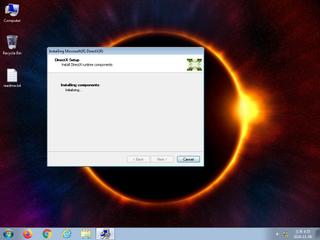
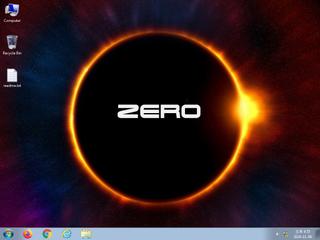
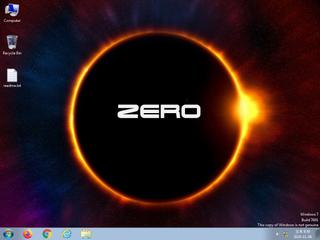
ScreenShot
| Created | 2024.11.08 17:14 | Machine | s1_win7_x6403 |
| Filename | dxwebsetup.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 66 detected (NeshtaB, Neshta, Malicious, score, HLLP, Venus, Unsafe, confidence, 100%, Delf, Neshuta, Windows, Apanas, Winlock, fmobyw, CLASSIC, Real Protect, high, ransomware, Renamer, Detected, A@3ypg, OBIX, GenAsa, Mo0tdcmmg3o, Infector, Gen9) | ||
| md5 | 2cca969570717a0af4f2531eb69cc7c9 | ||
| sha256 | a9971d2f3b8c1611723938a3ea6578c27f31049d3297e607cf0ee6927a4a26c7 | ||
| ssdeep | 6144:k9Qc2liXmrLxcdRDLiH1vVRGVOhMp421/7YQxhWK87:BcvgLARDI1KIOzOl | ||
| imphash | 9f4693fc0c511135129493f2161d1e86 | ||
| impfuzzy | 48:8cfpH9rngO0Mw+4Qk90pvn3O4Ga5tQ4w6T3:8cfpHZgO0MJ430pv3l | ||
Network IP location
Signature (11cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 66 AntiVirus engines on VirusTotal as malicious |
| watch | Installs itself for autorun at Windows startup |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | Steals private information from local Internet browsers |
| info | Checks amount of memory in system |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | Tries to locate where the browsers are installed |
Rules (33cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Emotet_1_Zero | Win32 Trojan Emotet | binaries (download) |
| danger | Win32_Trojan_Emotet_2_Zero | Win32 Trojan Emotet | binaries (download) |
| danger | Win32_Trojan_Emotet_RL_Gen_Zero | Win32 Trojan Emotet | binaries (download) |
| danger | Win32_Trojan_Emotet_RL_Gen_Zero | Win32 Trojan Emotet | binaries (upload) |
| danger | Win32_Trojan_Gen_1_0904B0_Zero | Win32 Trojan Emotet | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | NMap | NMAP | binaries (download) |
| warning | NSIS_Installer | Null Soft Installer | binaries (download) |
| warning | PhysicalDrive_20181001 | (no description) | binaries (download) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (download) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | ASPack_Zero | ASPack packed file | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | Network_Downloader | File Downloader | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | Win32_Trojan_PWS_Net_1_Zero | Win32 Trojan PWS .NET Azorult | binaries (download) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (download) |
| notice | Javascript_Blob | use blob(Binary Large Objec) javascript | binaries (download) |
| info | CAB_file_format | CAB archive file | binaries (download) |
| info | CAB_file_format | CAB archive file | binaries (upload) |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (download) |
| info | ftp_command | ftp command | binaries (download) |
| info | HWP_file_format | HWP Document File | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | Javascript_ActiveXObject | Use ActiveXObject JavaScript | binaries (download) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (download) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
kernel32.dll
0x4150dc DeleteCriticalSection
0x4150e0 LeaveCriticalSection
0x4150e4 EnterCriticalSection
0x4150e8 InitializeCriticalSection
0x4150ec VirtualFree
0x4150f0 VirtualAlloc
0x4150f4 LocalFree
0x4150f8 LocalAlloc
0x4150fc GetVersion
0x415100 GetCurrentThreadId
0x415104 GetThreadLocale
0x415108 GetStartupInfoA
0x41510c GetLocaleInfoA
0x415110 GetCommandLineA
0x415114 FreeLibrary
0x415118 ExitProcess
0x41511c WriteFile
0x415120 UnhandledExceptionFilter
0x415124 RtlUnwind
0x415128 RaiseException
0x41512c GetStdHandle
user32.dll
0x415134 GetKeyboardType
0x415138 MessageBoxA
advapi32.dll
0x415140 RegQueryValueExA
0x415144 RegOpenKeyExA
0x415148 RegCloseKey
oleaut32.dll
0x415150 SysFreeString
0x415154 SysReAllocStringLen
kernel32.dll
0x41515c TlsSetValue
0x415160 TlsGetValue
0x415164 LocalAlloc
0x415168 GetModuleHandleA
advapi32.dll
0x415170 RegSetValueExA
0x415174 RegOpenKeyExA
0x415178 RegCloseKey
kernel32.dll
0x415180 WriteFile
0x415184 WinExec
0x415188 SetFilePointer
0x41518c SetFileAttributesA
0x415190 SetEndOfFile
0x415194 SetCurrentDirectoryA
0x415198 ReleaseMutex
0x41519c ReadFile
0x4151a0 GetWindowsDirectoryA
0x4151a4 GetTempPathA
0x4151a8 GetShortPathNameA
0x4151ac GetModuleFileNameA
0x4151b0 GetLogicalDriveStringsA
0x4151b4 GetLocalTime
0x4151b8 GetLastError
0x4151bc GetFileSize
0x4151c0 GetFileAttributesA
0x4151c4 GetDriveTypeA
0x4151c8 GetCommandLineA
0x4151cc FreeLibrary
0x4151d0 FindNextFileA
0x4151d4 FindFirstFileA
0x4151d8 FindClose
0x4151dc DeleteFileA
0x4151e0 CreateMutexA
0x4151e4 CreateFileA
0x4151e8 CreateDirectoryA
0x4151ec CloseHandle
gdi32.dll
0x4151f4 StretchDIBits
0x4151f8 SetDIBits
0x4151fc SelectObject
0x415200 GetObjectA
0x415204 GetDIBits
0x415208 DeleteObject
0x41520c DeleteDC
0x415210 CreateSolidBrush
0x415214 CreateDIBSection
0x415218 CreateCompatibleDC
0x41521c CreateCompatibleBitmap
0x415220 BitBlt
user32.dll
0x415228 ReleaseDC
0x41522c GetSysColor
0x415230 GetIconInfo
0x415234 GetDC
0x415238 FillRect
0x41523c DestroyIcon
0x415240 CopyImage
0x415244 CharLowerBuffA
shell32.dll
0x41524c ShellExecuteA
0x415250 ExtractIconA
EAT(Export Address Table) is none
kernel32.dll
0x4150dc DeleteCriticalSection
0x4150e0 LeaveCriticalSection
0x4150e4 EnterCriticalSection
0x4150e8 InitializeCriticalSection
0x4150ec VirtualFree
0x4150f0 VirtualAlloc
0x4150f4 LocalFree
0x4150f8 LocalAlloc
0x4150fc GetVersion
0x415100 GetCurrentThreadId
0x415104 GetThreadLocale
0x415108 GetStartupInfoA
0x41510c GetLocaleInfoA
0x415110 GetCommandLineA
0x415114 FreeLibrary
0x415118 ExitProcess
0x41511c WriteFile
0x415120 UnhandledExceptionFilter
0x415124 RtlUnwind
0x415128 RaiseException
0x41512c GetStdHandle
user32.dll
0x415134 GetKeyboardType
0x415138 MessageBoxA
advapi32.dll
0x415140 RegQueryValueExA
0x415144 RegOpenKeyExA
0x415148 RegCloseKey
oleaut32.dll
0x415150 SysFreeString
0x415154 SysReAllocStringLen
kernel32.dll
0x41515c TlsSetValue
0x415160 TlsGetValue
0x415164 LocalAlloc
0x415168 GetModuleHandleA
advapi32.dll
0x415170 RegSetValueExA
0x415174 RegOpenKeyExA
0x415178 RegCloseKey
kernel32.dll
0x415180 WriteFile
0x415184 WinExec
0x415188 SetFilePointer
0x41518c SetFileAttributesA
0x415190 SetEndOfFile
0x415194 SetCurrentDirectoryA
0x415198 ReleaseMutex
0x41519c ReadFile
0x4151a0 GetWindowsDirectoryA
0x4151a4 GetTempPathA
0x4151a8 GetShortPathNameA
0x4151ac GetModuleFileNameA
0x4151b0 GetLogicalDriveStringsA
0x4151b4 GetLocalTime
0x4151b8 GetLastError
0x4151bc GetFileSize
0x4151c0 GetFileAttributesA
0x4151c4 GetDriveTypeA
0x4151c8 GetCommandLineA
0x4151cc FreeLibrary
0x4151d0 FindNextFileA
0x4151d4 FindFirstFileA
0x4151d8 FindClose
0x4151dc DeleteFileA
0x4151e0 CreateMutexA
0x4151e4 CreateFileA
0x4151e8 CreateDirectoryA
0x4151ec CloseHandle
gdi32.dll
0x4151f4 StretchDIBits
0x4151f8 SetDIBits
0x4151fc SelectObject
0x415200 GetObjectA
0x415204 GetDIBits
0x415208 DeleteObject
0x41520c DeleteDC
0x415210 CreateSolidBrush
0x415214 CreateDIBSection
0x415218 CreateCompatibleDC
0x41521c CreateCompatibleBitmap
0x415220 BitBlt
user32.dll
0x415228 ReleaseDC
0x41522c GetSysColor
0x415230 GetIconInfo
0x415234 GetDC
0x415238 FillRect
0x41523c DestroyIcon
0x415240 CopyImage
0x415244 CharLowerBuffA
shell32.dll
0x41524c ShellExecuteA
0x415250 ExtractIconA
EAT(Export Address Table) is none