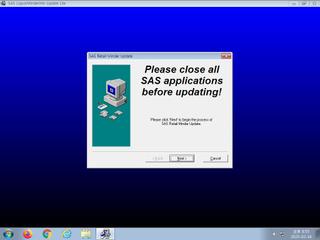
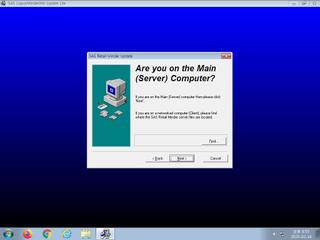
ScreenShot
| Created | 2025.02.18 17:41 | Machine | s1_win7_x6401 |
| Filename | update.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | 0c1d951bd8edb3b7ee31d34c543c3db3 | ||
| sha256 | f38ecda755dc8ba8825fb364c2f24ca53ed33ec01332238ac074afede77edb6b | ||
| ssdeep | 786432:ZFNLpFCkXnOgD/+BHmvWvzIivUGMjNV5A+TubYBoNVHQmb5YNyzombOn5PKNRYAn:ZFd+kXOgDg6AvMLv/aDrHQQYNEbffV | ||
| imphash | ef9b8e6863d1f74a617655ec935c6c32 | ||
| impfuzzy | 48:Ebik9gZQzOSt55uSe0Q4lCKKQ5QES5/1nBX4ozmb5EM:Ebb9gZQztaHxHmb5Z | ||
Network IP location
Signature (7cnts)
| Level | Description |
|---|---|
| watch | Creates an executable file in a user folder |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates executable files on the filesystem |
| notice | Drops an executable to the user AppData folder |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | The executable uses a known packer |
Rules (12cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x408060 SetErrorMode
0x408064 lstrcatA
0x408068 GetDriveTypeA
0x40806c SetEnvironmentVariableA
0x408070 lstrcpyA
0x408074 GetModuleFileNameA
0x408078 GetTempPathA
0x40807c GetTempFileNameA
0x408080 GlobalHandle
0x408084 _lwrite
0x408088 _lcreat
0x40808c _lopen
0x408090 _lclose
0x408094 WinExec
0x408098 GetEnvironmentVariableA
0x40809c RemoveDirectoryA
0x4080a0 CreateDirectoryA
0x4080a4 GetWindowsDirectoryA
0x4080a8 GetProcessHeap
0x4080ac ExitProcess
0x4080b0 TerminateProcess
0x4080b4 SetStdHandle
0x4080b8 SetFilePointer
0x4080bc FlushFileBuffers
0x4080c0 GetStringTypeA
0x4080c4 WriteFile
0x4080c8 GetStringTypeW
0x4080cc GetFileType
0x4080d0 GetStdHandle
0x4080d4 RtlUnwind
0x4080d8 GetEnvironmentStringsW
0x4080dc GetEnvironmentStrings
0x4080e0 SetHandleCount
0x4080e4 GlobalLock
0x4080e8 GetCurrentProcess
0x4080ec FreeEnvironmentStringsA
0x4080f0 UnhandledExceptionFilter
0x4080f4 FreeEnvironmentStringsW
0x4080f8 LCMapStringA
0x4080fc MultiByteToWideChar
0x408100 LCMapStringW
0x408104 GetVersionExA
0x408108 HeapAlloc
0x40810c GetCurrentThread
0x408110 CloseHandle
0x408114 HeapFree
0x408118 LoadLibraryA
0x40811c GetProcAddress
0x408120 GetCurrentThreadId
0x408124 FreeLibrary
0x408128 _lread
0x40812c _llseek
0x408130 GlobalUnlock
0x408134 GlobalFree
0x408138 GlobalAlloc
0x40813c HeapDestroy
0x408140 HeapCreate
0x408144 GetOEMCP
0x408148 GetLastError
0x40814c DeleteFileA
0x408150 GetModuleHandleA
0x408154 GetStartupInfoA
0x408158 GetCommandLineA
0x40815c GetVersion
0x408160 GetACP
0x408164 WideCharToMultiByte
0x408168 VirtualFree
0x40816c VirtualAlloc
0x408170 HeapReAlloc
0x408174 GetCPInfo
USER32.dll
0x40817c ReleaseDC
0x408180 ExitWindowsEx
0x408184 MessageBoxA
0x408188 LoadIconA
0x40818c RegisterClassA
0x408190 LoadCursorA
0x408194 SetWindowPos
0x408198 UpdateWindow
0x40819c ShowWindow
0x4081a0 wsprintfA
0x4081a4 LoadStringA
0x4081a8 InvalidateRect
0x4081ac BeginPaint
0x4081b0 EndPaint
0x4081b4 DefWindowProcA
0x4081b8 PostQuitMessage
0x4081bc SendMessageA
0x4081c0 GetDC
0x4081c4 GetClientRect
0x4081c8 CreateWindowExA
GDI32.dll
0x408038 GetDeviceCaps
0x40803c GetStockObject
0x408040 PatBlt
0x408044 DeleteObject
0x408048 SelectObject
0x40804c RealizePalette
0x408050 CreateSolidBrush
0x408054 CreatePalette
0x408058 SelectPalette
ADVAPI32.dll
0x408000 SetSecurityDescriptorDacl
0x408004 AllocateAndInitializeSid
0x408008 GetLengthSid
0x40800c InitializeAcl
0x408010 AddAccessAllowedAce
0x408014 InitializeSecurityDescriptor
0x408018 RevertToSelf
0x40801c SetSecurityDescriptorOwner
0x408020 SetSecurityDescriptorGroup
0x408024 ImpersonateSelf
0x408028 OpenThreadToken
0x40802c MapGenericMask
0x408030 AccessCheck
EAT(Export Address Table) Library
0x402a2c _MainWndProc@16
0x4030da _StubFileWrite@12
KERNEL32.dll
0x408060 SetErrorMode
0x408064 lstrcatA
0x408068 GetDriveTypeA
0x40806c SetEnvironmentVariableA
0x408070 lstrcpyA
0x408074 GetModuleFileNameA
0x408078 GetTempPathA
0x40807c GetTempFileNameA
0x408080 GlobalHandle
0x408084 _lwrite
0x408088 _lcreat
0x40808c _lopen
0x408090 _lclose
0x408094 WinExec
0x408098 GetEnvironmentVariableA
0x40809c RemoveDirectoryA
0x4080a0 CreateDirectoryA
0x4080a4 GetWindowsDirectoryA
0x4080a8 GetProcessHeap
0x4080ac ExitProcess
0x4080b0 TerminateProcess
0x4080b4 SetStdHandle
0x4080b8 SetFilePointer
0x4080bc FlushFileBuffers
0x4080c0 GetStringTypeA
0x4080c4 WriteFile
0x4080c8 GetStringTypeW
0x4080cc GetFileType
0x4080d0 GetStdHandle
0x4080d4 RtlUnwind
0x4080d8 GetEnvironmentStringsW
0x4080dc GetEnvironmentStrings
0x4080e0 SetHandleCount
0x4080e4 GlobalLock
0x4080e8 GetCurrentProcess
0x4080ec FreeEnvironmentStringsA
0x4080f0 UnhandledExceptionFilter
0x4080f4 FreeEnvironmentStringsW
0x4080f8 LCMapStringA
0x4080fc MultiByteToWideChar
0x408100 LCMapStringW
0x408104 GetVersionExA
0x408108 HeapAlloc
0x40810c GetCurrentThread
0x408110 CloseHandle
0x408114 HeapFree
0x408118 LoadLibraryA
0x40811c GetProcAddress
0x408120 GetCurrentThreadId
0x408124 FreeLibrary
0x408128 _lread
0x40812c _llseek
0x408130 GlobalUnlock
0x408134 GlobalFree
0x408138 GlobalAlloc
0x40813c HeapDestroy
0x408140 HeapCreate
0x408144 GetOEMCP
0x408148 GetLastError
0x40814c DeleteFileA
0x408150 GetModuleHandleA
0x408154 GetStartupInfoA
0x408158 GetCommandLineA
0x40815c GetVersion
0x408160 GetACP
0x408164 WideCharToMultiByte
0x408168 VirtualFree
0x40816c VirtualAlloc
0x408170 HeapReAlloc
0x408174 GetCPInfo
USER32.dll
0x40817c ReleaseDC
0x408180 ExitWindowsEx
0x408184 MessageBoxA
0x408188 LoadIconA
0x40818c RegisterClassA
0x408190 LoadCursorA
0x408194 SetWindowPos
0x408198 UpdateWindow
0x40819c ShowWindow
0x4081a0 wsprintfA
0x4081a4 LoadStringA
0x4081a8 InvalidateRect
0x4081ac BeginPaint
0x4081b0 EndPaint
0x4081b4 DefWindowProcA
0x4081b8 PostQuitMessage
0x4081bc SendMessageA
0x4081c0 GetDC
0x4081c4 GetClientRect
0x4081c8 CreateWindowExA
GDI32.dll
0x408038 GetDeviceCaps
0x40803c GetStockObject
0x408040 PatBlt
0x408044 DeleteObject
0x408048 SelectObject
0x40804c RealizePalette
0x408050 CreateSolidBrush
0x408054 CreatePalette
0x408058 SelectPalette
ADVAPI32.dll
0x408000 SetSecurityDescriptorDacl
0x408004 AllocateAndInitializeSid
0x408008 GetLengthSid
0x40800c InitializeAcl
0x408010 AddAccessAllowedAce
0x408014 InitializeSecurityDescriptor
0x408018 RevertToSelf
0x40801c SetSecurityDescriptorOwner
0x408020 SetSecurityDescriptorGroup
0x408024 ImpersonateSelf
0x408028 OpenThreadToken
0x40802c MapGenericMask
0x408030 AccessCheck
EAT(Export Address Table) Library
0x402a2c _MainWndProc@16
0x4030da _StubFileWrite@12