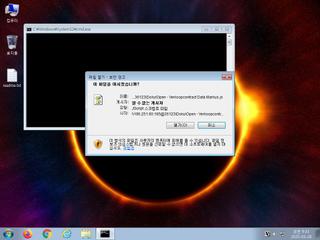
ScreenShot
| Created | 2025.03.28 09:40 | Machine | s1_win7_x6402 |
| Filename | Verkoopcontract Data Markus.pdf.lnk | ||
| Type | MS Windows shortcut, Points to a file or directory, Has Working directory, Icon number=11, Archive, ctime=Tue Mar 25 07:34:38 2025, mtime=Tue Mar 25 07:34:40 2025, atime=Tue Mar 25 07:34:40 2025, length=3143, window=hide | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | |||
| VT API (file) | |||
| md5 | 3bf01e91b90ca74b97bd244636d69ce5 | ||
| sha256 | 70e2d6287ccd9e78e4688e23755ba1132bd342399f0f3d79daa9988bd4518b7a | ||
| ssdeep | 24:8lvFjVddSBmEXuHYenvE583yUCj+7SBvMzgeNB3N/LVXsyiqDB3:8lvjdQBlXuH/vgU7Q2rnd | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (23cnts)
| Level | Description |
|---|---|
| danger | The processes wscript.exe |
| watch | Communicates with host for which no DNS query was performed |
| watch | Creates a suspicious Powershell process |
| watch | Enumerates services |
| watch | Harvests credentials from local email clients |
| watch | Network communications indicative of a potential document or script payload download was initiated by the process powershell.exe |
| watch | One or more non-whitelisted processes were created |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a shortcut to an executable file |
| notice | Creates a suspicious process |
| notice | Poweshell is sending data to a remote host |
| notice | URL downloaded by powershell script |
| notice | Uses Windows utilities for basic Windows functionality |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Command line console output was observed |
| info | Queries for the computername |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (35cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | Network_Downloader | File Downloader | memory |
| notice | Code_injection | Code injection with CreateRemoteThread in a remote process | memory |
| notice | Create_Service | Create a windows service | memory |
| notice | Escalate_priviledges | Escalate priviledges | memory |
| notice | Generic_PWS_Memory_Zero | PWS Memory | memory |
| notice | KeyLogger | Run a KeyLogger | memory |
| notice | local_credential_Steal | Steal credential | memory |
| notice | Network_DGA | Communication using DGA | memory |
| notice | Network_DNS | Communications use DNS | memory |
| notice | Network_FTP | Communications over FTP | memory |
| notice | Network_HTTP | Communications over HTTP | memory |
| notice | Network_P2P_Win | Communications over P2P network | memory |
| notice | Network_TCP_Socket | Communications over RAW Socket | memory |
| notice | ScreenShot | Take ScreenShot | memory |
| notice | Sniff_Audio | Record Audio | memory |
| notice | Str_Win32_Http_API | Match Windows Http API call | memory |
| notice | Str_Win32_Internet_API | Match Windows Inet API call | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | antisb_threatExpert | Anti-Sandbox checks for ThreatExpert | memory |
| info | Check_Dlls | (no description) | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerCheck__RemoteAPI | (no description) | memory |
| info | DebuggerException__ConsoleCtrl | (no description) | memory |
| info | DebuggerException__SetConsoleCtrl | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | lnk_file_format | Microsoft Windows Shortcut File Format | binaries (upload) |
| info | Lnk_Format_Zero | LNK Format | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | win_hook | Affect hook table | memory |
Network (11cnts) ?
Suricata ids
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET HUNTING Successful PROPFIND Response for Application Media Type
ET HUNTING PowerShell Hidden Window Command Common In Powershell Stagers M1
ET HUNTING Successful PROPFIND Response for Application Media Type
ET HUNTING PowerShell Hidden Window Command Common In Powershell Stagers M1