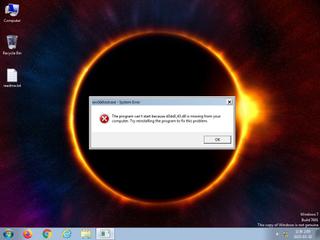
ScreenShot
| Created | 2025.03.30 14:11 | Machine | s1_win7_x6403 |
| Filename | wvckkhost.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 49 detected (AIDetectMalware, Malicious, score, Ghanarava, Lazy, Unsafe, confidence, 100%, Attribute, HighConfidence, high confidence, GenKryptik, HHNC, CrypterX, Sabsik, Kryptik, CLOUD, AGEN, moderate, Static AI, Suspicious PE, Detected, Wacatac, ABTrojan, JUKO, R693436, Artemis, Krypt, Chgt, PE04C9V, Gencirc, susgen) | ||
| md5 | cfc1981a3c3b8ddc41de5a60103f2250 | ||
| sha256 | 042ffb105b3f2ef6323986451ac747914bec45efde319cfa409a015b6a96c8c8 | ||
| ssdeep | 49152:rfHIOZyx3xOw1pY9DC2DvyxYAEMqv+LHtVT8+HEV/SoaplqeEKDVyqY6r:8MwYzv6YWHhpl1EKDVyUr | ||
| imphash | 7b9f795a11c3ef485f44ec2668b03d64 | ||
| impfuzzy | 192:qRWWVN9nTvKf3BetONRxGvaQqqwPpcnWvNEG:2WmN9nipAwx3vKG | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 49 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | This executable has a PDB path |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | ftp_command | ftp command | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
d3dx9_43.dll
0x140162de8 D3DXVec3Transform
0x140162df0 D3DXMatrixTranspose
0x140162df8 D3DXVec3Normalize
d3d11.dll
0x140162dc8 D3D11CreateDeviceAndSwapChain
KERNEL32.dll
0x1401621a0 FormatMessageA
0x1401621a8 ReleaseSRWLockExclusive
0x1401621b0 AcquireSRWLockExclusive
0x1401621b8 SleepConditionVariableSRW
0x1401621c0 GetCurrentThreadId
0x1401621c8 WakeAllConditionVariable
0x1401621d0 RtlCaptureContext
0x1401621d8 RtlLookupFunctionEntry
0x1401621e0 WaitForMultipleObjects
0x1401621e8 PeekNamedPipe
0x1401621f0 RtlVirtualUnwind
0x1401621f8 UnhandledExceptionFilter
0x140162200 SetUnhandledExceptionFilter
0x140162208 IsProcessorFeaturePresent
0x140162210 VirtualProtect
0x140162218 GetStartupInfoW
0x140162220 CheckRemoteDebuggerPresent
0x140162228 GetModuleHandleW
0x140162230 GetSystemTimeAsFileTime
0x140162238 GetEnvironmentVariableA
0x140162240 GetCurrentProcessId
0x140162248 WaitForSingleObjectEx
0x140162250 MoveFileExA
0x140162258 CreateRemoteThreadEx
0x140162260 QueryPerformanceCounter
0x140162268 FreeLibrary
0x140162270 VerifyVersionInfoA
0x140162278 VerSetConditionMask
0x140162280 QueryPerformanceFrequency
0x140162288 GetLocaleInfoA
0x140162290 GetSystemDirectoryA
0x140162298 WideCharToMultiByte
0x1401622a0 GlobalFree
0x1401622a8 MultiByteToWideChar
0x1401622b0 GetStartupInfoA
0x1401622b8 SleepEx
0x1401622c0 VirtualAlloc
0x1401622c8 CreateThread
0x1401622d0 EnterCriticalSection
0x1401622d8 IsDebuggerPresent
0x1401622e0 OpenThread
0x1401622e8 GetStdHandle
0x1401622f0 GetTickCount
0x1401622f8 DeleteCriticalSection
0x140162300 InitializeCriticalSectionEx
0x140162308 LeaveCriticalSection
0x140162310 GetTickCount64
0x140162318 GetProcAddress
0x140162320 LoadLibraryA
0x140162328 GetCommandLineA
0x140162330 GetModuleHandleA
0x140162338 GlobalUnlock
0x140162340 CreateRemoteThread
0x140162348 DuplicateHandle
0x140162350 GetProcessId
0x140162358 TerminateProcess
0x140162360 InitializeSListHead
0x140162368 ExitProcess
0x140162370 LocalFree
0x140162378 SetLastError
0x140162380 GlobalLock
0x140162388 Beep
0x140162390 GlobalAlloc
0x140162398 GetLastError
0x1401623a0 Sleep
0x1401623a8 GetCurrentProcess
0x1401623b0 ReadProcessMemory
0x1401623b8 VirtualProtectEx
0x1401623c0 CloseHandle
0x1401623c8 Process32Next
0x1401623d0 K32GetModuleFileNameExA
0x1401623d8 CreateToolhelp32Snapshot
0x1401623e0 OpenProcess
0x1401623e8 Module32First
0x1401623f0 Module32Next
0x1401623f8 HeapFree
0x140162400 WriteProcessMemory
0x140162408 Process32First
0x140162410 VirtualFreeEx
0x140162418 VirtualAllocEx
0x140162420 HeapAlloc
0x140162428 ReadFile
0x140162430 GetFileSizeEx
0x140162438 UnmapViewOfFile
0x140162440 MapViewOfFile
0x140162448 CreateFileA
0x140162450 GetFileType
0x140162458 CreateFileMappingA
USER32.dll
0x140162658 GetClipboardData
0x140162660 SetWindowDisplayAffinity
0x140162668 EmptyClipboard
0x140162670 CloseClipboard
0x140162678 SetWindowLongA
0x140162680 OpenClipboard
0x140162688 UpdateWindow
0x140162690 SetClipboardData
0x140162698 PostQuitMessage
0x1401626a0 GetWindowLongPtrA
0x1401626a8 PeekMessageA
0x1401626b0 GetForegroundWindow
0x1401626b8 SetLayeredWindowAttributes
0x1401626c0 DefWindowProcA
0x1401626c8 UnhookWindowsHookEx
0x1401626d0 mouse_event
0x1401626d8 FindWindowA
0x1401626e0 GetAsyncKeyState
0x1401626e8 MoveWindow
0x1401626f0 MessageBoxA
0x1401626f8 SetWindowsHookExA
0x140162700 ShowWindow
0x140162708 RegisterClassExW
0x140162710 UnregisterClassW
0x140162718 CallNextHookEx
0x140162720 PostMessageA
0x140162728 TranslateMessage
0x140162730 DestroyWindow
0x140162738 GetWindowRect
0x140162740 GetWindowThreadProcessId
0x140162748 IsWindowVisible
0x140162750 GetWindowTextA
0x140162758 EnumWindows
0x140162760 FindWindowW
0x140162768 SetWindowsHookA
0x140162770 DispatchMessageA
0x140162778 GetCursorPos
0x140162780 SetCursorPos
0x140162788 ReleaseCapture
0x140162790 IsWindowUnicode
0x140162798 GetClientRect
0x1401627a0 SetCursor
0x1401627a8 SetCapture
0x1401627b0 GetKeyboardLayout
0x1401627b8 TrackMouseEvent
0x1401627c0 ClientToScreen
0x1401627c8 GetCapture
0x1401627d0 ScreenToClient
0x1401627d8 LoadCursorA
0x1401627e0 GetMessageExtraInfo
0x1401627e8 GetWindowTextLengthA
0x1401627f0 GetKeyState
ADVAPI32.dll
0x140162000 AdjustTokenPrivileges
0x140162008 CryptReleaseContext
0x140162010 CryptGetHashParam
0x140162018 CryptGenRandom
0x140162020 CryptCreateHash
0x140162028 CryptHashData
0x140162030 CryptDestroyHash
0x140162038 CryptDestroyKey
0x140162040 CryptImportKey
0x140162048 CryptEncrypt
0x140162050 GetTokenInformation
0x140162058 QueryServiceStatus
0x140162060 CloseServiceHandle
0x140162068 OpenSCManagerA
0x140162070 ControlService
0x140162078 OpenServiceA
0x140162080 RevertToSelf
0x140162088 CreateProcessAsUserA
0x140162090 RegGetValueA
0x140162098 PrivilegeCheck
0x1401620a0 SetTokenInformation
0x1401620a8 LookupPrivilegeValueA
0x1401620b0 SetThreadToken
0x1401620b8 DuplicateTokenEx
0x1401620c0 ConvertSidToStringSidA
0x1401620c8 OpenProcessToken
0x1401620d0 CryptAcquireContextA
ole32.dll
0x140162e30 CoInitializeEx
MSVCP140.dll
0x140162468 ?_Id_cnt@id@locale@std@@0HA
0x140162470 ?_Xout_of_range@std@@YAXPEBD@Z
0x140162478 ?_Ipfx@?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA_N_N@Z
0x140162480 ?snextc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x140162488 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x140162490 ?sgetc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x140162498 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1401624a0 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1401624a8 ??0?$basic_iostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@@Z
0x1401624b0 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1401624b8 ?_Lock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x1401624c0 ?_Unlock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x1401624c8 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x1401624d0 ?uflow@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x1401624d8 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x1401624e0 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x1401624e8 ?setbuf@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAPEAV12@PEAD_J@Z
0x1401624f0 ?sync@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x1401624f8 ?imbue@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAXAEBVlocale@2@@Z
0x140162500 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x140162508 ??1?$basic_iostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x140162510 ??Bios_base@std@@QEBA_NXZ
0x140162518 ?uncaught_exceptions@std@@YAHXZ
0x140162520 ?_Xbad_function_call@std@@YAXXZ
0x140162528 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x140162530 _Thrd_detach
0x140162538 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x140162540 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x140162548 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x140162550 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x140162558 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAVios_base@1@AEAV21@@Z@Z
0x140162560 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEAI@Z
0x140162568 ?good@ios_base@std@@QEBA_NXZ
0x140162570 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x140162578 ?_Fiopen@std@@YAPEAU_iobuf@@PEBDHH@Z
0x140162580 ??1_Lockit@std@@QEAA@XZ
0x140162588 ?widen@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADD@Z
0x140162590 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x140162598 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x1401625a0 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x1401625a8 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXPEAPEAD0PEAH001@Z
0x1401625b0 ??0?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x1401625b8 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1401625c0 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1401625c8 ?sbumpc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x1401625d0 ??1?$basic_istream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1401625d8 ??7ios_base@std@@QEBA_NXZ
0x1401625e0 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x1401625e8 ?_Random_device@std@@YAIXZ
0x1401625f0 _Mtx_unlock
0x1401625f8 _Mtx_lock
0x140162600 ?_Xlength_error@std@@YAXPEBD@Z
0x140162608 ?_Throw_Cpp_error@std@@YAXH@Z
0x140162610 _Query_perf_counter
0x140162618 ?_Xbad_alloc@std@@YAXXZ
0x140162620 _Query_perf_frequency
0x140162628 _Cnd_do_broadcast_at_thread_exit
0x140162630 ??0_Lockit@std@@QEAA@H@Z
0x140162638 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
d3dx11_43.dll
0x140162dd8 D3DX11CreateShaderResourceViewFromMemory
WS2_32.dll
0x140162940 gethostname
0x140162948 closesocket
0x140162950 recv
0x140162958 send
0x140162960 WSAGetLastError
0x140162968 ind
0x140162970 connect
0x140162978 getpeername
0x140162980 getsockname
0x140162988 getsockopt
0x140162990 ntohl
0x140162998 htons
0x1401629a0 sendto
0x1401629a8 recvfrom
0x1401629b0 freeaddrinfo
0x1401629b8 getaddrinfo
0x1401629c0 select
0x1401629c8 __WSAFDIsSet
0x1401629d0 ioctlsocket
0x1401629d8 listen
0x1401629e0 htonl
0x1401629e8 accept
0x1401629f0 WSACleanup
0x1401629f8 WSAStartup
0x140162a00 WSAIoctl
0x140162a08 WSASetLastError
0x140162a10 socket
0x140162a18 setsockopt
0x140162a20 ntohs
Normaliz.dll
0x140162648 IdnToAscii
CRYPT32.dll
0x1401620e0 CryptQueryObject
0x1401620e8 CertCreateCertificateChainEngine
0x1401620f0 CertFreeCertificateChainEngine
0x1401620f8 CertGetCertificateChain
0x140162100 CertFreeCertificateChain
0x140162108 CertOpenStore
0x140162110 CertGetNameStringA
0x140162118 CertEnumCertificatesInStore
0x140162120 CertFindCertificateInStore
0x140162128 CertFreeCertificateContext
0x140162130 CryptStringToBinaryA
0x140162138 PFXImportCertStore
0x140162140 CryptDecodeObjectEx
0x140162148 CertAddCertificateContextToStore
0x140162150 CertCloseStore
0x140162158 CertFindExtension
WLDAP32.dll
0x1401628a8 None
0x1401628b0 None
0x1401628b8 None
0x1401628c0 None
0x1401628c8 None
0x1401628d0 None
0x1401628d8 None
0x1401628e0 None
0x1401628e8 None
0x1401628f0 None
0x1401628f8 None
0x140162900 None
0x140162908 None
0x140162910 None
0x140162918 None
0x140162920 None
0x140162928 None
0x140162930 None
ntdll.dll
0x140162e18 ZwReadVirtualMemory
0x140162e20 ZwWriteVirtualMemory
IMM32.dll
0x140162178 ImmSetCandidateWindow
0x140162180 ImmReleaseContext
0x140162188 ImmGetContext
0x140162190 ImmSetCompositionWindow
D3DCOMPILER_43.dll
0x140162168 D3DCompile
dwmapi.dll
0x140162e08 DwmExtendFrameIntoClientArea
VCRUNTIME140_1.dll
0x140162898 __CxxFrameHandler4
VCRUNTIME140.dll
0x140162800 _CxxThrowException
0x140162808 __intrinsic_setjmp
0x140162810 __current_exception_context
0x140162818 __current_exception
0x140162820 __C_specific_handler
0x140162828 memcmp
0x140162830 memchr
0x140162838 memset
0x140162840 memmove
0x140162848 memcpy
0x140162850 longjmp
0x140162858 strrchr
0x140162860 __std_exception_destroy
0x140162868 __std_exception_copy
0x140162870 __std_terminate
0x140162878 strstr
0x140162880 strchr
0x140162888 wcsstr
api-ms-win-crt-heap-l1-1-0.dll
0x140162ab8 _set_new_mode
0x140162ac0 realloc
0x140162ac8 malloc
0x140162ad0 _callnewh
0x140162ad8 free
0x140162ae0 calloc
api-ms-win-crt-runtime-l1-1-0.dll
0x140162b80 strerror
0x140162b88 _c_exit
0x140162b90 _register_thread_local_exe_atexit_callback
0x140162b98 _get_narrow_winmain_command_line
0x140162ba0 _set_app_type
0x140162ba8 _getpid
0x140162bb0 _invalid_parameter_noinfo_noreturn
0x140162bb8 _seh_filter_exe
0x140162bc0 _cexit
0x140162bc8 _exit
0x140162bd0 terminate
0x140162bd8 _configure_narrow_argv
0x140162be0 _initialize_narrow_environment
0x140162be8 _errno
0x140162bf0 _crt_atexit
0x140162bf8 _initterm_e
0x140162c00 exit
0x140162c08 _register_onexit_function
0x140162c10 __sys_nerr
0x140162c18 _beginthreadex
0x140162c20 _initialize_onexit_table
0x140162c28 _initterm
api-ms-win-crt-string-l1-1-0.dll
0x140162d38 strncpy
0x140162d40 strncmp
0x140162d48 strcpy_s
0x140162d50 strcmp
0x140162d58 tolower
0x140162d60 strpbrk
0x140162d68 _stricmp
0x140162d70 strcspn
0x140162d78 strspn
0x140162d80 isupper
0x140162d88 _strdup
0x140162d90 toupper
api-ms-win-crt-convert-l1-1-0.dll
0x140162a30 strtoull
0x140162a38 atof
0x140162a40 strtod
0x140162a48 strtol
0x140162a50 strtoul
0x140162a58 strtoll
0x140162a60 atoi
api-ms-win-crt-math-l1-1-0.dll
0x140162b08 fmodf
0x140162b10 powf
0x140162b18 sinf
0x140162b20 sqrt
0x140162b28 cosf
0x140162b30 ceilf
0x140162b38 atan2f
0x140162b40 acosf
0x140162b48 _hypotf
0x140162b50 _dsign
0x140162b58 __setusermatherr
0x140162b60 sqrtf
api-ms-win-crt-stdio-l1-1-0.dll
0x140162c38 _open
0x140162c40 _close
0x140162c48 _write
0x140162c50 _read
0x140162c58 __stdio_common_vsprintf
0x140162c60 fputc
0x140162c68 __p__commode
0x140162c70 _lseeki64
0x140162c78 fflush
0x140162c80 fgets
0x140162c88 fclose
0x140162c90 _set_fmode
0x140162c98 feof
0x140162ca0 fgetc
0x140162ca8 fputs
0x140162cb0 fopen
0x140162cb8 fwrite
0x140162cc0 fgetpos
0x140162cc8 setvbuf
0x140162cd0 __stdio_common_vsscanf
0x140162cd8 _wfopen
0x140162ce0 ungetc
0x140162ce8 fsetpos
0x140162cf0 __stdio_common_vfprintf
0x140162cf8 fseek
0x140162d00 __acrt_iob_func
0x140162d08 ftell
0x140162d10 _get_stream_buffer_pointers
0x140162d18 _fseeki64
0x140162d20 __stdio_common_vsprintf_s
0x140162d28 fread
api-ms-win-crt-locale-l1-1-0.dll
0x140162af0 _configthreadlocale
0x140162af8 localeconv
api-ms-win-crt-filesystem-l1-1-0.dll
0x140162a80 _unlock_file
0x140162a88 _fstat64
0x140162a90 _lock_file
0x140162a98 _stat64
0x140162aa0 _unlink
0x140162aa8 _access
api-ms-win-crt-multibyte-l1-1-0.dll
0x140162b70 _mbsicmp
api-ms-win-crt-utility-l1-1-0.dll
0x140162db8 qsort
api-ms-win-crt-environment-l1-1-0.dll
0x140162a70 getenv
api-ms-win-crt-time-l1-1-0.dll
0x140162da0 _gmtime64
0x140162da8 _time64
EAT(Export Address Table) is none
d3dx9_43.dll
0x140162de8 D3DXVec3Transform
0x140162df0 D3DXMatrixTranspose
0x140162df8 D3DXVec3Normalize
d3d11.dll
0x140162dc8 D3D11CreateDeviceAndSwapChain
KERNEL32.dll
0x1401621a0 FormatMessageA
0x1401621a8 ReleaseSRWLockExclusive
0x1401621b0 AcquireSRWLockExclusive
0x1401621b8 SleepConditionVariableSRW
0x1401621c0 GetCurrentThreadId
0x1401621c8 WakeAllConditionVariable
0x1401621d0 RtlCaptureContext
0x1401621d8 RtlLookupFunctionEntry
0x1401621e0 WaitForMultipleObjects
0x1401621e8 PeekNamedPipe
0x1401621f0 RtlVirtualUnwind
0x1401621f8 UnhandledExceptionFilter
0x140162200 SetUnhandledExceptionFilter
0x140162208 IsProcessorFeaturePresent
0x140162210 VirtualProtect
0x140162218 GetStartupInfoW
0x140162220 CheckRemoteDebuggerPresent
0x140162228 GetModuleHandleW
0x140162230 GetSystemTimeAsFileTime
0x140162238 GetEnvironmentVariableA
0x140162240 GetCurrentProcessId
0x140162248 WaitForSingleObjectEx
0x140162250 MoveFileExA
0x140162258 CreateRemoteThreadEx
0x140162260 QueryPerformanceCounter
0x140162268 FreeLibrary
0x140162270 VerifyVersionInfoA
0x140162278 VerSetConditionMask
0x140162280 QueryPerformanceFrequency
0x140162288 GetLocaleInfoA
0x140162290 GetSystemDirectoryA
0x140162298 WideCharToMultiByte
0x1401622a0 GlobalFree
0x1401622a8 MultiByteToWideChar
0x1401622b0 GetStartupInfoA
0x1401622b8 SleepEx
0x1401622c0 VirtualAlloc
0x1401622c8 CreateThread
0x1401622d0 EnterCriticalSection
0x1401622d8 IsDebuggerPresent
0x1401622e0 OpenThread
0x1401622e8 GetStdHandle
0x1401622f0 GetTickCount
0x1401622f8 DeleteCriticalSection
0x140162300 InitializeCriticalSectionEx
0x140162308 LeaveCriticalSection
0x140162310 GetTickCount64
0x140162318 GetProcAddress
0x140162320 LoadLibraryA
0x140162328 GetCommandLineA
0x140162330 GetModuleHandleA
0x140162338 GlobalUnlock
0x140162340 CreateRemoteThread
0x140162348 DuplicateHandle
0x140162350 GetProcessId
0x140162358 TerminateProcess
0x140162360 InitializeSListHead
0x140162368 ExitProcess
0x140162370 LocalFree
0x140162378 SetLastError
0x140162380 GlobalLock
0x140162388 Beep
0x140162390 GlobalAlloc
0x140162398 GetLastError
0x1401623a0 Sleep
0x1401623a8 GetCurrentProcess
0x1401623b0 ReadProcessMemory
0x1401623b8 VirtualProtectEx
0x1401623c0 CloseHandle
0x1401623c8 Process32Next
0x1401623d0 K32GetModuleFileNameExA
0x1401623d8 CreateToolhelp32Snapshot
0x1401623e0 OpenProcess
0x1401623e8 Module32First
0x1401623f0 Module32Next
0x1401623f8 HeapFree
0x140162400 WriteProcessMemory
0x140162408 Process32First
0x140162410 VirtualFreeEx
0x140162418 VirtualAllocEx
0x140162420 HeapAlloc
0x140162428 ReadFile
0x140162430 GetFileSizeEx
0x140162438 UnmapViewOfFile
0x140162440 MapViewOfFile
0x140162448 CreateFileA
0x140162450 GetFileType
0x140162458 CreateFileMappingA
USER32.dll
0x140162658 GetClipboardData
0x140162660 SetWindowDisplayAffinity
0x140162668 EmptyClipboard
0x140162670 CloseClipboard
0x140162678 SetWindowLongA
0x140162680 OpenClipboard
0x140162688 UpdateWindow
0x140162690 SetClipboardData
0x140162698 PostQuitMessage
0x1401626a0 GetWindowLongPtrA
0x1401626a8 PeekMessageA
0x1401626b0 GetForegroundWindow
0x1401626b8 SetLayeredWindowAttributes
0x1401626c0 DefWindowProcA
0x1401626c8 UnhookWindowsHookEx
0x1401626d0 mouse_event
0x1401626d8 FindWindowA
0x1401626e0 GetAsyncKeyState
0x1401626e8 MoveWindow
0x1401626f0 MessageBoxA
0x1401626f8 SetWindowsHookExA
0x140162700 ShowWindow
0x140162708 RegisterClassExW
0x140162710 UnregisterClassW
0x140162718 CallNextHookEx
0x140162720 PostMessageA
0x140162728 TranslateMessage
0x140162730 DestroyWindow
0x140162738 GetWindowRect
0x140162740 GetWindowThreadProcessId
0x140162748 IsWindowVisible
0x140162750 GetWindowTextA
0x140162758 EnumWindows
0x140162760 FindWindowW
0x140162768 SetWindowsHookA
0x140162770 DispatchMessageA
0x140162778 GetCursorPos
0x140162780 SetCursorPos
0x140162788 ReleaseCapture
0x140162790 IsWindowUnicode
0x140162798 GetClientRect
0x1401627a0 SetCursor
0x1401627a8 SetCapture
0x1401627b0 GetKeyboardLayout
0x1401627b8 TrackMouseEvent
0x1401627c0 ClientToScreen
0x1401627c8 GetCapture
0x1401627d0 ScreenToClient
0x1401627d8 LoadCursorA
0x1401627e0 GetMessageExtraInfo
0x1401627e8 GetWindowTextLengthA
0x1401627f0 GetKeyState
ADVAPI32.dll
0x140162000 AdjustTokenPrivileges
0x140162008 CryptReleaseContext
0x140162010 CryptGetHashParam
0x140162018 CryptGenRandom
0x140162020 CryptCreateHash
0x140162028 CryptHashData
0x140162030 CryptDestroyHash
0x140162038 CryptDestroyKey
0x140162040 CryptImportKey
0x140162048 CryptEncrypt
0x140162050 GetTokenInformation
0x140162058 QueryServiceStatus
0x140162060 CloseServiceHandle
0x140162068 OpenSCManagerA
0x140162070 ControlService
0x140162078 OpenServiceA
0x140162080 RevertToSelf
0x140162088 CreateProcessAsUserA
0x140162090 RegGetValueA
0x140162098 PrivilegeCheck
0x1401620a0 SetTokenInformation
0x1401620a8 LookupPrivilegeValueA
0x1401620b0 SetThreadToken
0x1401620b8 DuplicateTokenEx
0x1401620c0 ConvertSidToStringSidA
0x1401620c8 OpenProcessToken
0x1401620d0 CryptAcquireContextA
ole32.dll
0x140162e30 CoInitializeEx
MSVCP140.dll
0x140162468 ?_Id_cnt@id@locale@std@@0HA
0x140162470 ?_Xout_of_range@std@@YAXPEBD@Z
0x140162478 ?_Ipfx@?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA_N_N@Z
0x140162480 ?snextc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x140162488 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x140162490 ?sgetc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x140162498 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1401624a0 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1401624a8 ??0?$basic_iostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@@Z
0x1401624b0 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1401624b8 ?_Lock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x1401624c0 ?_Unlock@?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAAXXZ
0x1401624c8 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x1401624d0 ?uflow@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x1401624d8 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x1401624e0 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x1401624e8 ?setbuf@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAPEAV12@PEAD_J@Z
0x1401624f0 ?sync@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAHXZ
0x1401624f8 ?imbue@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAXAEBVlocale@2@@Z
0x140162500 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x140162508 ??1?$basic_iostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x140162510 ??Bios_base@std@@QEBA_NXZ
0x140162518 ?uncaught_exceptions@std@@YAHXZ
0x140162520 ?_Xbad_function_call@std@@YAXXZ
0x140162528 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x140162530 _Thrd_detach
0x140162538 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x140162540 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x140162548 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x140162550 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x140162558 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAVios_base@1@AEAV21@@Z@Z
0x140162560 ??5?$basic_istream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@AEAI@Z
0x140162568 ?good@ios_base@std@@QEBA_NXZ
0x140162570 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x140162578 ?_Fiopen@std@@YAPEAU_iobuf@@PEBDHH@Z
0x140162580 ??1_Lockit@std@@QEAA@XZ
0x140162588 ?widen@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADD@Z
0x140162590 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x140162598 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x1401625a0 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x1401625a8 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXPEAPEAD0PEAH001@Z
0x1401625b0 ??0?$basic_istream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x1401625b8 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1401625c0 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1401625c8 ?sbumpc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ
0x1401625d0 ??1?$basic_istream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1401625d8 ??7ios_base@std@@QEBA_NXZ
0x1401625e0 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x1401625e8 ?_Random_device@std@@YAIXZ
0x1401625f0 _Mtx_unlock
0x1401625f8 _Mtx_lock
0x140162600 ?_Xlength_error@std@@YAXPEBD@Z
0x140162608 ?_Throw_Cpp_error@std@@YAXH@Z
0x140162610 _Query_perf_counter
0x140162618 ?_Xbad_alloc@std@@YAXXZ
0x140162620 _Query_perf_frequency
0x140162628 _Cnd_do_broadcast_at_thread_exit
0x140162630 ??0_Lockit@std@@QEAA@H@Z
0x140162638 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
d3dx11_43.dll
0x140162dd8 D3DX11CreateShaderResourceViewFromMemory
WS2_32.dll
0x140162940 gethostname
0x140162948 closesocket
0x140162950 recv
0x140162958 send
0x140162960 WSAGetLastError
0x140162968 ind
0x140162970 connect
0x140162978 getpeername
0x140162980 getsockname
0x140162988 getsockopt
0x140162990 ntohl
0x140162998 htons
0x1401629a0 sendto
0x1401629a8 recvfrom
0x1401629b0 freeaddrinfo
0x1401629b8 getaddrinfo
0x1401629c0 select
0x1401629c8 __WSAFDIsSet
0x1401629d0 ioctlsocket
0x1401629d8 listen
0x1401629e0 htonl
0x1401629e8 accept
0x1401629f0 WSACleanup
0x1401629f8 WSAStartup
0x140162a00 WSAIoctl
0x140162a08 WSASetLastError
0x140162a10 socket
0x140162a18 setsockopt
0x140162a20 ntohs
Normaliz.dll
0x140162648 IdnToAscii
CRYPT32.dll
0x1401620e0 CryptQueryObject
0x1401620e8 CertCreateCertificateChainEngine
0x1401620f0 CertFreeCertificateChainEngine
0x1401620f8 CertGetCertificateChain
0x140162100 CertFreeCertificateChain
0x140162108 CertOpenStore
0x140162110 CertGetNameStringA
0x140162118 CertEnumCertificatesInStore
0x140162120 CertFindCertificateInStore
0x140162128 CertFreeCertificateContext
0x140162130 CryptStringToBinaryA
0x140162138 PFXImportCertStore
0x140162140 CryptDecodeObjectEx
0x140162148 CertAddCertificateContextToStore
0x140162150 CertCloseStore
0x140162158 CertFindExtension
WLDAP32.dll
0x1401628a8 None
0x1401628b0 None
0x1401628b8 None
0x1401628c0 None
0x1401628c8 None
0x1401628d0 None
0x1401628d8 None
0x1401628e0 None
0x1401628e8 None
0x1401628f0 None
0x1401628f8 None
0x140162900 None
0x140162908 None
0x140162910 None
0x140162918 None
0x140162920 None
0x140162928 None
0x140162930 None
ntdll.dll
0x140162e18 ZwReadVirtualMemory
0x140162e20 ZwWriteVirtualMemory
IMM32.dll
0x140162178 ImmSetCandidateWindow
0x140162180 ImmReleaseContext
0x140162188 ImmGetContext
0x140162190 ImmSetCompositionWindow
D3DCOMPILER_43.dll
0x140162168 D3DCompile
dwmapi.dll
0x140162e08 DwmExtendFrameIntoClientArea
VCRUNTIME140_1.dll
0x140162898 __CxxFrameHandler4
VCRUNTIME140.dll
0x140162800 _CxxThrowException
0x140162808 __intrinsic_setjmp
0x140162810 __current_exception_context
0x140162818 __current_exception
0x140162820 __C_specific_handler
0x140162828 memcmp
0x140162830 memchr
0x140162838 memset
0x140162840 memmove
0x140162848 memcpy
0x140162850 longjmp
0x140162858 strrchr
0x140162860 __std_exception_destroy
0x140162868 __std_exception_copy
0x140162870 __std_terminate
0x140162878 strstr
0x140162880 strchr
0x140162888 wcsstr
api-ms-win-crt-heap-l1-1-0.dll
0x140162ab8 _set_new_mode
0x140162ac0 realloc
0x140162ac8 malloc
0x140162ad0 _callnewh
0x140162ad8 free
0x140162ae0 calloc
api-ms-win-crt-runtime-l1-1-0.dll
0x140162b80 strerror
0x140162b88 _c_exit
0x140162b90 _register_thread_local_exe_atexit_callback
0x140162b98 _get_narrow_winmain_command_line
0x140162ba0 _set_app_type
0x140162ba8 _getpid
0x140162bb0 _invalid_parameter_noinfo_noreturn
0x140162bb8 _seh_filter_exe
0x140162bc0 _cexit
0x140162bc8 _exit
0x140162bd0 terminate
0x140162bd8 _configure_narrow_argv
0x140162be0 _initialize_narrow_environment
0x140162be8 _errno
0x140162bf0 _crt_atexit
0x140162bf8 _initterm_e
0x140162c00 exit
0x140162c08 _register_onexit_function
0x140162c10 __sys_nerr
0x140162c18 _beginthreadex
0x140162c20 _initialize_onexit_table
0x140162c28 _initterm
api-ms-win-crt-string-l1-1-0.dll
0x140162d38 strncpy
0x140162d40 strncmp
0x140162d48 strcpy_s
0x140162d50 strcmp
0x140162d58 tolower
0x140162d60 strpbrk
0x140162d68 _stricmp
0x140162d70 strcspn
0x140162d78 strspn
0x140162d80 isupper
0x140162d88 _strdup
0x140162d90 toupper
api-ms-win-crt-convert-l1-1-0.dll
0x140162a30 strtoull
0x140162a38 atof
0x140162a40 strtod
0x140162a48 strtol
0x140162a50 strtoul
0x140162a58 strtoll
0x140162a60 atoi
api-ms-win-crt-math-l1-1-0.dll
0x140162b08 fmodf
0x140162b10 powf
0x140162b18 sinf
0x140162b20 sqrt
0x140162b28 cosf
0x140162b30 ceilf
0x140162b38 atan2f
0x140162b40 acosf
0x140162b48 _hypotf
0x140162b50 _dsign
0x140162b58 __setusermatherr
0x140162b60 sqrtf
api-ms-win-crt-stdio-l1-1-0.dll
0x140162c38 _open
0x140162c40 _close
0x140162c48 _write
0x140162c50 _read
0x140162c58 __stdio_common_vsprintf
0x140162c60 fputc
0x140162c68 __p__commode
0x140162c70 _lseeki64
0x140162c78 fflush
0x140162c80 fgets
0x140162c88 fclose
0x140162c90 _set_fmode
0x140162c98 feof
0x140162ca0 fgetc
0x140162ca8 fputs
0x140162cb0 fopen
0x140162cb8 fwrite
0x140162cc0 fgetpos
0x140162cc8 setvbuf
0x140162cd0 __stdio_common_vsscanf
0x140162cd8 _wfopen
0x140162ce0 ungetc
0x140162ce8 fsetpos
0x140162cf0 __stdio_common_vfprintf
0x140162cf8 fseek
0x140162d00 __acrt_iob_func
0x140162d08 ftell
0x140162d10 _get_stream_buffer_pointers
0x140162d18 _fseeki64
0x140162d20 __stdio_common_vsprintf_s
0x140162d28 fread
api-ms-win-crt-locale-l1-1-0.dll
0x140162af0 _configthreadlocale
0x140162af8 localeconv
api-ms-win-crt-filesystem-l1-1-0.dll
0x140162a80 _unlock_file
0x140162a88 _fstat64
0x140162a90 _lock_file
0x140162a98 _stat64
0x140162aa0 _unlink
0x140162aa8 _access
api-ms-win-crt-multibyte-l1-1-0.dll
0x140162b70 _mbsicmp
api-ms-win-crt-utility-l1-1-0.dll
0x140162db8 qsort
api-ms-win-crt-environment-l1-1-0.dll
0x140162a70 getenv
api-ms-win-crt-time-l1-1-0.dll
0x140162da0 _gmtime64
0x140162da8 _time64
EAT(Export Address Table) is none