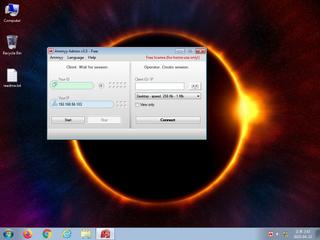
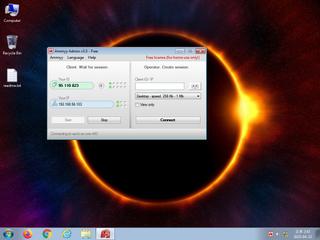
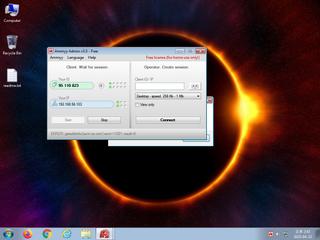
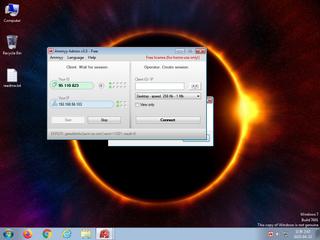
ScreenShot
| Created | 2025.04.23 14:46 | Machine | s1_win7_x6403 |
| Filename | mscorsvw1.log | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | b3b9eb83af47770dbb8e86f95afe9634 | ||
| sha256 | 58d939306109bc6626c75ce7ef4ea4615229ca90ba246197427d40ba0197c8e5 | ||
| ssdeep | 98304:aBWUc7GXJhjlaXSvIsadQre5PaRB30ONA4+tIPx7l+7k0yuDB8d:8VT/CSAsayreYb308Dpn0zDB | ||
| imphash | a63be339d6242a8f92508baf82eec945 | ||
| impfuzzy | 24:1r+Nz2uQG1PssKL+cOPqEWLKvQaQtXJHc9NDI5Q8:tozvQG1PxgWvQnXpcM5Q8 | ||
Network IP location
Signature (12cnts)
| Level | Description |
|---|---|
| watch | Installs itself for autorun at Windows startup |
| watch | Queries information on disks |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Creates a service |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Sends data using the HTTP POST Method |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is likely packed with VMProtect |
| info | Checks amount of memory in system |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| watch | VMProtect_Zero | VMProtect packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
WS2_32.dll
0xbf8000 WSAGetLastError
GDI32.dll
0xbf8008 GetDIBits
USER32.dll
0xbf8010 FindWindowA
SHELL32.dll
0xbf8018 SHBrowseForFolderW
MSVCP60.dll
0xbf8020 ??1Init@ios_base@std@@QAE@XZ
MSVCRT.dll
0xbf8028 _strnicmp
Secur32.dll
0xbf8030 FreeCredentialsHandle
SETUPAPI.dll
0xbf8038 SetupDiEnumDeviceInfo
iphlpapi.dll
0xbf8040 GetAdaptersInfo
ADVAPI32.dll
0xbf8048 RegOpenKeyExA
SHLWAPI.dll
0xbf8050 PathGetDriveNumberA
comdlg32.dll
0xbf8058 GetOpenFileNameW
USERENV.dll
0xbf8060 LoadUserProfileA
COMCTL32.dll
0xbf8068 CreateToolbarEx
WININET.dll
0xbf8070 HttpSendRequestA
DSOUND.dll
0xbf8078 None
KERNEL32.dll
0xbf8080 GetVersionExA
WTSAPI32.dll
0xbf8088 WTSSendMessageW
KERNEL32.dll
0xbf8090 VirtualQuery
USER32.dll
0xbf8098 GetUserObjectInformationW
KERNEL32.dll
0xbf80a0 LocalAlloc
0xbf80a4 LocalFree
0xbf80a8 GetModuleFileNameW
0xbf80ac GetProcessAffinityMask
0xbf80b0 SetProcessAffinityMask
0xbf80b4 SetThreadAffinityMask
0xbf80b8 Sleep
0xbf80bc ExitProcess
0xbf80c0 FreeLibrary
0xbf80c4 LoadLibraryA
0xbf80c8 GetModuleHandleA
0xbf80cc GetProcAddress
USER32.dll
0xbf80d4 GetProcessWindowStation
0xbf80d8 GetUserObjectInformationW
EAT(Export Address Table) is none
WS2_32.dll
0xbf8000 WSAGetLastError
GDI32.dll
0xbf8008 GetDIBits
USER32.dll
0xbf8010 FindWindowA
SHELL32.dll
0xbf8018 SHBrowseForFolderW
MSVCP60.dll
0xbf8020 ??1Init@ios_base@std@@QAE@XZ
MSVCRT.dll
0xbf8028 _strnicmp
Secur32.dll
0xbf8030 FreeCredentialsHandle
SETUPAPI.dll
0xbf8038 SetupDiEnumDeviceInfo
iphlpapi.dll
0xbf8040 GetAdaptersInfo
ADVAPI32.dll
0xbf8048 RegOpenKeyExA
SHLWAPI.dll
0xbf8050 PathGetDriveNumberA
comdlg32.dll
0xbf8058 GetOpenFileNameW
USERENV.dll
0xbf8060 LoadUserProfileA
COMCTL32.dll
0xbf8068 CreateToolbarEx
WININET.dll
0xbf8070 HttpSendRequestA
DSOUND.dll
0xbf8078 None
KERNEL32.dll
0xbf8080 GetVersionExA
WTSAPI32.dll
0xbf8088 WTSSendMessageW
KERNEL32.dll
0xbf8090 VirtualQuery
USER32.dll
0xbf8098 GetUserObjectInformationW
KERNEL32.dll
0xbf80a0 LocalAlloc
0xbf80a4 LocalFree
0xbf80a8 GetModuleFileNameW
0xbf80ac GetProcessAffinityMask
0xbf80b0 SetProcessAffinityMask
0xbf80b4 SetThreadAffinityMask
0xbf80b8 Sleep
0xbf80bc ExitProcess
0xbf80c0 FreeLibrary
0xbf80c4 LoadLibraryA
0xbf80c8 GetModuleHandleA
0xbf80cc GetProcAddress
USER32.dll
0xbf80d4 GetProcessWindowStation
0xbf80d8 GetUserObjectInformationW
EAT(Export Address Table) is none