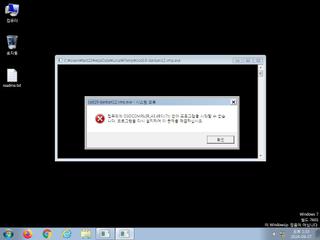
ScreenShot
| Created | 2024.09.27 13:46 | Machine | s1_win7_x6401 |
| Filename | cod19-danban12.vmp.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 23 detected (AIDetectMalware, Malicious, score, Unsafe, confidence, Attribute, HighConfidence, high confidence, VMProtect, L suspicious, AGEN, Real Protect, high, Static AI, Suspicious PE, Detected, Caypnamer, VMProtBad, Eldorado, R663373, Artemis) | ||
| md5 | 6b1daab5a1d25a65a3ff7a6b753468fd | ||
| sha256 | be493fddd2bc9bc6d4e186f4698db3022b811baa47f6552bf6cec03e472069e3 | ||
| ssdeep | 196608:lAuRXHdU8e2+LAlqMU1m9HxwDVf2KVYSCZROiEFikVQ:lT3dU8e2+Y9HxC1CZROBYki | ||
| imphash | 11ae26485c0cac468c08d19a4378636d | ||
| impfuzzy | 24:2WzAbjD5GBu5bJZYMu5FO58QtXJHc9NDI5Q8:jkjEoZYMt5ZXpcM5Q8 | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 23 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is likely packed with VMProtect |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | VMProtect_Zero | VMProtect packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
d3d11.dll
0x1406b2000 D3D11CreateDeviceAndSwapChain
D3DCOMPILER_43.dll
0x1406b2010 D3DCompile
IMM32.dll
0x1406b2020 ImmSetCompositionWindow
WINHTTP.dll
0x1406b2030 WinHttpOpenRequest
KERNEL32.dll
0x1406b2040 UnhandledExceptionFilter
USER32.dll
0x1406b2050 GetMessageA
ADVAPI32.dll
0x1406b2060 RegCreateKeyW
MSVCP140.dll
0x1406b2070 ?setbuf@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAPEAV12@PEAD_J@Z
ntdll.dll
0x1406b2080 RtlVirtualUnwind
WS2_32.dll
0x1406b2090 inet_addr
VCRUNTIME140_1.dll
0x1406b20a0 __CxxFrameHandler4
VCRUNTIME140.dll
0x1406b20b0 memcmp
api-ms-win-crt-runtime-l1-1-0.dll
0x1406b20c0 _invalid_parameter_noinfo_noreturn
api-ms-win-crt-stdio-l1-1-0.dll
0x1406b20d0 fopen
api-ms-win-crt-string-l1-1-0.dll
0x1406b20e0 _stricmp
api-ms-win-crt-utility-l1-1-0.dll
0x1406b20f0 rand
api-ms-win-crt-heap-l1-1-0.dll
0x1406b2100 realloc
api-ms-win-crt-convert-l1-1-0.dll
0x1406b2110 strtod
api-ms-win-crt-filesystem-l1-1-0.dll
0x1406b2120 _lock_file
api-ms-win-crt-time-l1-1-0.dll
0x1406b2130 _time64
api-ms-win-crt-math-l1-1-0.dll
0x1406b2140 fmod
api-ms-win-crt-locale-l1-1-0.dll
0x1406b2150 _configthreadlocale
WTSAPI32.dll
0x1406b2160 WTSSendMessageW
KERNEL32.dll
0x1406b2170 FlsSetValue
USER32.dll
0x1406b2180 GetProcessWindowStation
KERNEL32.dll
0x1406b2190 LocalAlloc
0x1406b2198 LocalFree
0x1406b21a0 GetModuleFileNameW
0x1406b21a8 GetProcessAffinityMask
0x1406b21b0 SetProcessAffinityMask
0x1406b21b8 SetThreadAffinityMask
0x1406b21c0 Sleep
0x1406b21c8 ExitProcess
0x1406b21d0 FreeLibrary
0x1406b21d8 LoadLibraryA
0x1406b21e0 GetModuleHandleA
0x1406b21e8 GetProcAddress
USER32.dll
0x1406b21f8 GetProcessWindowStation
0x1406b2200 GetUserObjectInformationW
EAT(Export Address Table) Library
0x140054550 cJSON_AddArrayToObject
0x140054140 cJSON_AddBoolToObject
0x140054060 cJSON_AddFalseToObject
0x140053dd0 cJSON_AddItemReferenceToArray
0x140053e50 cJSON_AddItemReferenceToObject
0x140053c30 cJSON_AddItemToArray
0x140053d90 cJSON_AddItemToObject
0x140053db0 cJSON_AddItemToObjectCS
0x140053ea0 cJSON_AddNullToObject
0x140054230 cJSON_AddNumberToObject
0x140054470 cJSON_AddObjectToObject
0x1400543b0 cJSON_AddRawToObject
0x1400542f0 cJSON_AddStringToObject
0x140053f80 cJSON_AddTrueToObject
0x140055ae0 cJSON_Compare
0x140055190 cJSON_CreateArray
0x140055040 cJSON_CreateArrayReference
0x140054dc0 cJSON_CreateBool
0x140055490 cJSON_CreateDoubleArray
0x140054d80 cJSON_CreateFalse
0x140055350 cJSON_CreateFloatArray
0x140055210 cJSON_CreateIntArray
0x140054d00 cJSON_CreateNull
0x140054e00 cJSON_CreateNumber
0x1400551d0 cJSON_CreateObject
0x140054ff0 cJSON_CreateObjectReference
0x140055090 cJSON_CreateRaw
0x140054ea0 cJSON_CreateString
0x1400555c0 cJSON_CreateStringArray
0x140054fa0 cJSON_CreateStringReference
0x140054d40 cJSON_CreateTrue
0x140051b40 cJSON_Delete
0x140054740 cJSON_DeleteItemFromArray
0x1400548e0 cJSON_DeleteItemFromObject
0x140054970 cJSON_DeleteItemFromObjectCaseSensitive
0x1400546a0 cJSON_DetachItemFromArray
0x1400547d0 cJSON_DetachItemFromObject
0x140054850 cJSON_DetachItemFromObjectCaseSensitive
0x140054630 cJSON_DetachItemViaPointer
0x1400556f0 cJSON_Duplicate
0x140053a30 cJSON_GetArrayItem
0x140053a10 cJSON_GetArraySize
0x140051a00 cJSON_GetErrorPtr
0x140051a30 cJSON_GetNumberValue
0x140053b80 cJSON_GetObjectItem
0x140053b90 cJSON_GetObjectItemCaseSensitive
0x140051a10 cJSON_GetStringValue
0x140053ba0 cJSON_HasObjectItem
0x140051aa0 cJSON_InitHooks
0x140054a00 cJSON_InsertItemInArray
0x140055ab0 cJSON_IsArray
0x140055a60 cJSON_IsBool
0x140055a40 cJSON_IsFalse
0x140055a30 cJSON_IsInvalid
0x140055a80 cJSON_IsNull
0x140055a90 cJSON_IsNumber
0x140055ac0 cJSON_IsObject
0x140055ad0 cJSON_IsRaw
0x140055aa0 cJSON_IsString
0x140055a50 cJSON_IsTrue
0x1400558f0 cJSON_Minify
0x1400529e0 cJSON_Parse
0x140052a10 cJSON_ParseWithLength
0x140052780 cJSON_ParseWithLengthOpts
0x140052750 cJSON_ParseWithOpts
0x140052b60 cJSON_Print
0x140052b80 cJSON_PrintBuffered
0x140052c40 cJSON_PrintPreallocated
0x140052b70 cJSON_PrintUnformatted
0x140054bc0 cJSON_ReplaceItemInArray
0x140054ce0 cJSON_ReplaceItemInObject
0x140054cf0 cJSON_ReplaceItemInObjectCaseSensitive
0x140054ab0 cJSON_ReplaceItemViaPointer
0x140051bc0 cJSON_SetNumberHelper
0x140051c00 cJSON_SetValuestring
0x140051a50 cJSON_Version
0x140055e00 cJSON_free
0x140055df0 cJSON_malloc
d3d11.dll
0x1406b2000 D3D11CreateDeviceAndSwapChain
D3DCOMPILER_43.dll
0x1406b2010 D3DCompile
IMM32.dll
0x1406b2020 ImmSetCompositionWindow
WINHTTP.dll
0x1406b2030 WinHttpOpenRequest
KERNEL32.dll
0x1406b2040 UnhandledExceptionFilter
USER32.dll
0x1406b2050 GetMessageA
ADVAPI32.dll
0x1406b2060 RegCreateKeyW
MSVCP140.dll
0x1406b2070 ?setbuf@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAAPEAV12@PEAD_J@Z
ntdll.dll
0x1406b2080 RtlVirtualUnwind
WS2_32.dll
0x1406b2090 inet_addr
VCRUNTIME140_1.dll
0x1406b20a0 __CxxFrameHandler4
VCRUNTIME140.dll
0x1406b20b0 memcmp
api-ms-win-crt-runtime-l1-1-0.dll
0x1406b20c0 _invalid_parameter_noinfo_noreturn
api-ms-win-crt-stdio-l1-1-0.dll
0x1406b20d0 fopen
api-ms-win-crt-string-l1-1-0.dll
0x1406b20e0 _stricmp
api-ms-win-crt-utility-l1-1-0.dll
0x1406b20f0 rand
api-ms-win-crt-heap-l1-1-0.dll
0x1406b2100 realloc
api-ms-win-crt-convert-l1-1-0.dll
0x1406b2110 strtod
api-ms-win-crt-filesystem-l1-1-0.dll
0x1406b2120 _lock_file
api-ms-win-crt-time-l1-1-0.dll
0x1406b2130 _time64
api-ms-win-crt-math-l1-1-0.dll
0x1406b2140 fmod
api-ms-win-crt-locale-l1-1-0.dll
0x1406b2150 _configthreadlocale
WTSAPI32.dll
0x1406b2160 WTSSendMessageW
KERNEL32.dll
0x1406b2170 FlsSetValue
USER32.dll
0x1406b2180 GetProcessWindowStation
KERNEL32.dll
0x1406b2190 LocalAlloc
0x1406b2198 LocalFree
0x1406b21a0 GetModuleFileNameW
0x1406b21a8 GetProcessAffinityMask
0x1406b21b0 SetProcessAffinityMask
0x1406b21b8 SetThreadAffinityMask
0x1406b21c0 Sleep
0x1406b21c8 ExitProcess
0x1406b21d0 FreeLibrary
0x1406b21d8 LoadLibraryA
0x1406b21e0 GetModuleHandleA
0x1406b21e8 GetProcAddress
USER32.dll
0x1406b21f8 GetProcessWindowStation
0x1406b2200 GetUserObjectInformationW
EAT(Export Address Table) Library
0x140054550 cJSON_AddArrayToObject
0x140054140 cJSON_AddBoolToObject
0x140054060 cJSON_AddFalseToObject
0x140053dd0 cJSON_AddItemReferenceToArray
0x140053e50 cJSON_AddItemReferenceToObject
0x140053c30 cJSON_AddItemToArray
0x140053d90 cJSON_AddItemToObject
0x140053db0 cJSON_AddItemToObjectCS
0x140053ea0 cJSON_AddNullToObject
0x140054230 cJSON_AddNumberToObject
0x140054470 cJSON_AddObjectToObject
0x1400543b0 cJSON_AddRawToObject
0x1400542f0 cJSON_AddStringToObject
0x140053f80 cJSON_AddTrueToObject
0x140055ae0 cJSON_Compare
0x140055190 cJSON_CreateArray
0x140055040 cJSON_CreateArrayReference
0x140054dc0 cJSON_CreateBool
0x140055490 cJSON_CreateDoubleArray
0x140054d80 cJSON_CreateFalse
0x140055350 cJSON_CreateFloatArray
0x140055210 cJSON_CreateIntArray
0x140054d00 cJSON_CreateNull
0x140054e00 cJSON_CreateNumber
0x1400551d0 cJSON_CreateObject
0x140054ff0 cJSON_CreateObjectReference
0x140055090 cJSON_CreateRaw
0x140054ea0 cJSON_CreateString
0x1400555c0 cJSON_CreateStringArray
0x140054fa0 cJSON_CreateStringReference
0x140054d40 cJSON_CreateTrue
0x140051b40 cJSON_Delete
0x140054740 cJSON_DeleteItemFromArray
0x1400548e0 cJSON_DeleteItemFromObject
0x140054970 cJSON_DeleteItemFromObjectCaseSensitive
0x1400546a0 cJSON_DetachItemFromArray
0x1400547d0 cJSON_DetachItemFromObject
0x140054850 cJSON_DetachItemFromObjectCaseSensitive
0x140054630 cJSON_DetachItemViaPointer
0x1400556f0 cJSON_Duplicate
0x140053a30 cJSON_GetArrayItem
0x140053a10 cJSON_GetArraySize
0x140051a00 cJSON_GetErrorPtr
0x140051a30 cJSON_GetNumberValue
0x140053b80 cJSON_GetObjectItem
0x140053b90 cJSON_GetObjectItemCaseSensitive
0x140051a10 cJSON_GetStringValue
0x140053ba0 cJSON_HasObjectItem
0x140051aa0 cJSON_InitHooks
0x140054a00 cJSON_InsertItemInArray
0x140055ab0 cJSON_IsArray
0x140055a60 cJSON_IsBool
0x140055a40 cJSON_IsFalse
0x140055a30 cJSON_IsInvalid
0x140055a80 cJSON_IsNull
0x140055a90 cJSON_IsNumber
0x140055ac0 cJSON_IsObject
0x140055ad0 cJSON_IsRaw
0x140055aa0 cJSON_IsString
0x140055a50 cJSON_IsTrue
0x1400558f0 cJSON_Minify
0x1400529e0 cJSON_Parse
0x140052a10 cJSON_ParseWithLength
0x140052780 cJSON_ParseWithLengthOpts
0x140052750 cJSON_ParseWithOpts
0x140052b60 cJSON_Print
0x140052b80 cJSON_PrintBuffered
0x140052c40 cJSON_PrintPreallocated
0x140052b70 cJSON_PrintUnformatted
0x140054bc0 cJSON_ReplaceItemInArray
0x140054ce0 cJSON_ReplaceItemInObject
0x140054cf0 cJSON_ReplaceItemInObjectCaseSensitive
0x140054ab0 cJSON_ReplaceItemViaPointer
0x140051bc0 cJSON_SetNumberHelper
0x140051c00 cJSON_SetValuestring
0x140051a50 cJSON_Version
0x140055e00 cJSON_free
0x140055df0 cJSON_malloc