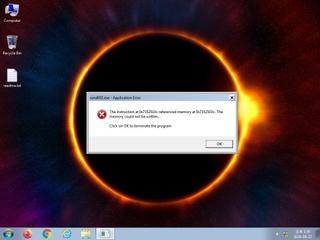
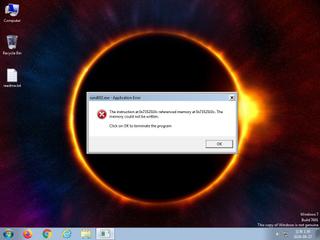
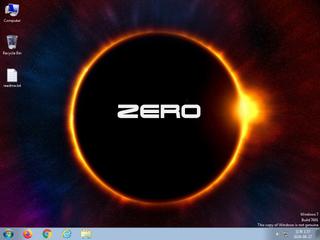
ScreenShot
| Created | 2024.09.27 13:48 | Machine | s1_win7_x6403 |
| Filename | payload.dll | ||
| Type | PE32 executable (DLL) (GUI) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 26 detected (AIDetectMalware, Dump, Sliver, Marte, HackTool, Implant, 64bit, uwccg, a variant of WinGo, MalwareX, Vilers, Tool, SBeacon, Static AI, Malicious PE, Detected, SuspGolang, 5VSUHL, Yfow) | ||
| md5 | c994bb9982dd689598c6c261090a40cb | ||
| sha256 | fbce9fc010fdfb67da5ff95cc5a5d1dbb0c07950522f130b031e55831f81b060 | ||
| ssdeep | 196608:rcRl1WLHnSCf24VHfaRpamWwSOsPlebA:8CLkGMadfNgb | ||
| imphash | 7d61210a06b412428471240387e6e605 | ||
| impfuzzy | 24:nJ614djMCutrMBqCDNQkaV6+kLLq3TydX8JOmc3bVjan9J9NJlDvlxcqcfZy:nJbFMCg1r6+kFdX8JOmL9J9NJlDvkqco | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| danger | Connects to IP addresses that are no longer responding to requests (legitimate services will remain up-and-running usually) |
| warning | File has been identified by 26 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| watch | Detects the presence of Wine emulator |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (6cnts) ?
Suricata ids
SURICATA Applayer Mismatch protocol both directions
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x69307180 AddVectoredExceptionHandler
0x69307184 CloseHandle
0x69307188 CreateEventA
0x6930718c CreateFileA
0x69307190 CreateIoCompletionPort
0x69307194 CreateThread
0x69307198 CreateWaitableTimerExW
0x6930719c DeleteCriticalSection
0x693071a0 DuplicateHandle
0x693071a4 EnterCriticalSection
0x693071a8 ExitProcess
0x693071ac FreeEnvironmentStringsW
0x693071b0 FreeLibrary
0x693071b4 GetConsoleMode
0x693071b8 GetEnvironmentStringsW
0x693071bc GetLastError
0x693071c0 GetModuleHandleA
0x693071c4 GetModuleHandleW
0x693071c8 GetProcAddress
0x693071cc GetProcessAffinityMask
0x693071d0 GetQueuedCompletionStatusEx
0x693071d4 GetStdHandle
0x693071d8 GetSystemDirectoryA
0x693071dc GetSystemInfo
0x693071e0 GetThreadContext
0x693071e4 InitializeCriticalSection
0x693071e8 IsDBCSLeadByteEx
0x693071ec LeaveCriticalSection
0x693071f0 LoadLibraryA
0x693071f4 LoadLibraryW
0x693071f8 MultiByteToWideChar
0x693071fc PostQueuedCompletionStatus
0x69307200 ResumeThread
0x69307204 SetConsoleCtrlHandler
0x69307208 SetErrorMode
0x6930720c SetEvent
0x69307210 SetProcessPriorityBoost
0x69307214 SetThreadContext
0x69307218 SetUnhandledExceptionFilter
0x6930721c SetWaitableTimer
0x69307220 Sleep
0x69307224 SuspendThread
0x69307228 SwitchToThread
0x6930722c TlsGetValue
0x69307230 VirtualAlloc
0x69307234 VirtualFree
0x69307238 VirtualProtect
0x6930723c VirtualQuery
0x69307240 WaitForMultipleObjects
0x69307244 WaitForSingleObject
0x69307248 WideCharToMultiByte
0x6930724c WriteConsoleW
0x69307250 WriteFile
msvcrt.dll
0x69307258 __mb_cur_max
0x6930725c _amsg_exit
0x69307260 _beginthread
0x69307264 _errno
0x69307268 _initterm
0x6930726c _iob
0x69307270 _lock
0x69307274 _unlock
0x69307278 abort
0x6930727c atoi
0x69307280 calloc
0x69307284 fputc
0x69307288 free
0x6930728c fwrite
0x69307290 localeconv
0x69307294 malloc
0x69307298 memcpy
0x6930729c memset
0x693072a0 realloc
0x693072a4 setlocale
0x693072a8 strchr
0x693072ac strerror
0x693072b0 strlen
0x693072b4 strncmp
0x693072b8 vfprintf
0x693072bc wcslen
EAT(Export Address Table) Library
0x68d15140 DllInstall
0x68d15190 DllRegisterServer
0x68d151e0 DllUnregisterServer
0x68d150a0 StartW
0x68d150f0 VoidFunc
0x6930510c _cgo_dummy_export
KERNEL32.dll
0x69307180 AddVectoredExceptionHandler
0x69307184 CloseHandle
0x69307188 CreateEventA
0x6930718c CreateFileA
0x69307190 CreateIoCompletionPort
0x69307194 CreateThread
0x69307198 CreateWaitableTimerExW
0x6930719c DeleteCriticalSection
0x693071a0 DuplicateHandle
0x693071a4 EnterCriticalSection
0x693071a8 ExitProcess
0x693071ac FreeEnvironmentStringsW
0x693071b0 FreeLibrary
0x693071b4 GetConsoleMode
0x693071b8 GetEnvironmentStringsW
0x693071bc GetLastError
0x693071c0 GetModuleHandleA
0x693071c4 GetModuleHandleW
0x693071c8 GetProcAddress
0x693071cc GetProcessAffinityMask
0x693071d0 GetQueuedCompletionStatusEx
0x693071d4 GetStdHandle
0x693071d8 GetSystemDirectoryA
0x693071dc GetSystemInfo
0x693071e0 GetThreadContext
0x693071e4 InitializeCriticalSection
0x693071e8 IsDBCSLeadByteEx
0x693071ec LeaveCriticalSection
0x693071f0 LoadLibraryA
0x693071f4 LoadLibraryW
0x693071f8 MultiByteToWideChar
0x693071fc PostQueuedCompletionStatus
0x69307200 ResumeThread
0x69307204 SetConsoleCtrlHandler
0x69307208 SetErrorMode
0x6930720c SetEvent
0x69307210 SetProcessPriorityBoost
0x69307214 SetThreadContext
0x69307218 SetUnhandledExceptionFilter
0x6930721c SetWaitableTimer
0x69307220 Sleep
0x69307224 SuspendThread
0x69307228 SwitchToThread
0x6930722c TlsGetValue
0x69307230 VirtualAlloc
0x69307234 VirtualFree
0x69307238 VirtualProtect
0x6930723c VirtualQuery
0x69307240 WaitForMultipleObjects
0x69307244 WaitForSingleObject
0x69307248 WideCharToMultiByte
0x6930724c WriteConsoleW
0x69307250 WriteFile
msvcrt.dll
0x69307258 __mb_cur_max
0x6930725c _amsg_exit
0x69307260 _beginthread
0x69307264 _errno
0x69307268 _initterm
0x6930726c _iob
0x69307270 _lock
0x69307274 _unlock
0x69307278 abort
0x6930727c atoi
0x69307280 calloc
0x69307284 fputc
0x69307288 free
0x6930728c fwrite
0x69307290 localeconv
0x69307294 malloc
0x69307298 memcpy
0x6930729c memset
0x693072a0 realloc
0x693072a4 setlocale
0x693072a8 strchr
0x693072ac strerror
0x693072b0 strlen
0x693072b4 strncmp
0x693072b8 vfprintf
0x693072bc wcslen
EAT(Export Address Table) Library
0x68d15140 DllInstall
0x68d15190 DllRegisterServer
0x68d151e0 DllUnregisterServer
0x68d150a0 StartW
0x68d150f0 VoidFunc
0x6930510c _cgo_dummy_export