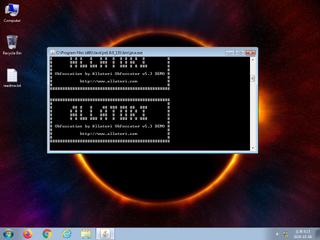
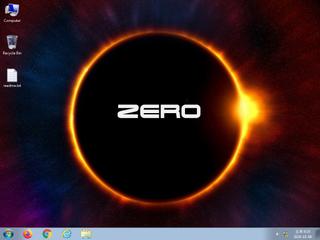
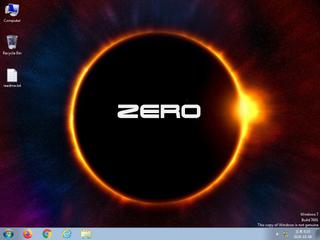
ScreenShot
| Created | 2024.10.06 18:25 | Machine | s1_win7_x6403 |
| Filename | 185.jar | ||
| Type | Zip archive data, at least v2.0 to extract | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 18 detected (Malicious, score, Artemis, a variant of Java, Kryptik, Java, QRat, mrucl, Detected, S5JGEN, Ktgl) | ||
| md5 | 29fd6772aafb08c90b1ff9a91f48ecff | ||
| sha256 | 287e892aeb4be05c881e19da227d0398cd321d5a9af837932c12dfaab641b4cb | ||
| ssdeep | 393216:hU+MrvMUXlIm0QEiK4JISelo4pOT0w03Bl:hSIelIvgJYlIIF3/ | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (19cnts)
| Level | Description |
|---|---|
| warning | Generates some ICMP traffic |
| watch | Attempts to identify installed AV products by installation directory |
| watch | Communicates with host for which no DNS query was performed |
| watch | Creates a windows hook that monitors keyboard input (keylogger) |
| watch | File has been identified by 18 AntiVirus engines on VirusTotal as malicious |
| watch | Installs an hook procedure to monitor for mouse events |
| watch | The processes java.exe |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Creates executable files on the filesystem |
| notice | Drops an executable to the user AppData folder |
| notice | Starts servers listening |
| notice | Steals private information from local Internet browsers |
| notice | Uses Windows utilities for basic Windows functionality |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Command line console output was observed |
| info | One or more processes crashed |
Rules (10cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | zip_file_format | ZIP file format | binaries (download) |
| info | zip_file_format | ZIP file format | binaries (upload) |