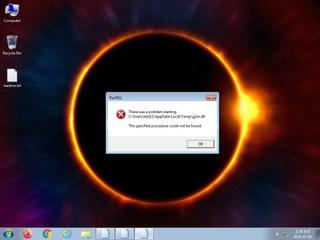
ScreenShot
| Created | 2024.10.08 21:57 | Machine | s1_win7_x6403 |
| Filename | g2m.dll | ||
| Type | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 15 detected (AIDetectMalware, Malicious, score, Lazy, high confidence, Wacatac, R663456) | ||
| md5 | e0fa9d4894017e66af927bd72df16793 | ||
| sha256 | fca664019d4465e2f9382c47da8acdf6739ee598191bd748c836a5f752031ad2 | ||
| ssdeep | 49152:j2lwbRru3gdv1++5k0IqjtDs7s42D8QpIgRc+6XndpCMid7oywkcnQ1S4KF:64RS34x5dh3qXnbo5cnQ | ||
| imphash | caf16897a970a8f4155bada10fad09fd | ||
| impfuzzy | 48:/FT+gpS71XhwROq9L/yBjkfsw0QuKVURWWTgHolW9xvYwVS:/FT+gI5XhwRNdgj08W9HmW9xvhS | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 15 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | One or more processes crashed |
| info | This executable has a PDB path |
Rules (8cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
USER32.dll
0x101cd000 ShowWindow
api-ms-win-core-synch-l1-2-0.dll
0x101cd040 WaitOnAddress
0x101cd044 WakeByAddressAll
0x101cd048 WakeByAddressSingle
cryptprimitives.dll
0x101cd094 ProcessPrng
kernel32.dll
0x101cd0cc QueryPerformanceFrequency
0x101cd0d0 UnhandledExceptionFilter
0x101cd0d4 SetHandleInformation
0x101cd0d8 SetUnhandledExceptionFilter
0x101cd0dc IsProcessorFeaturePresent
0x101cd0e0 GetCurrentThreadId
0x101cd0e4 InitializeSListHead
0x101cd0e8 GetFileInformationByHandle
0x101cd0ec GetConsoleWindow
0x101cd0f0 GetProcAddress
0x101cd0f4 LoadLibraryA
0x101cd0f8 CloseHandle
0x101cd0fc GetConsoleMode
0x101cd100 IsDebuggerPresent
0x101cd104 CreateIoCompletionPort
0x101cd108 GetQueuedCompletionStatusEx
0x101cd10c PostQueuedCompletionStatus
0x101cd110 SetFileCompletionNotificationModes
0x101cd114 QueryPerformanceCounter
0x101cd118 GetNativeSystemInfo
0x101cd11c VirtualQuery
0x101cd120 VirtualAlloc
0x101cd124 VirtualFree
0x101cd128 VirtualProtect
0x101cd12c GetSystemInfo
0x101cd130 CreateFileMappingW
0x101cd134 MapViewOfFile
0x101cd138 UnmapViewOfFile
0x101cd13c GetSystemTimeAsFileTime
0x101cd140 FreeEnvironmentStringsW
0x101cd144 DeleteProcThreadAttributeList
0x101cd148 CompareStringOrdinal
0x101cd14c GetLastError
0x101cd150 SetThreadStackGuarantee
0x101cd154 GetCurrentThread
0x101cd158 SwitchToThread
0x101cd15c WaitForSingleObject
0x101cd160 GetCurrentProcess
0x101cd164 RtlCaptureContext
0x101cd168 ReleaseMutex
0x101cd16c SetLastError
0x101cd170 GetCurrentDirectoryW
0x101cd174 GetEnvironmentStringsW
0x101cd178 GetEnvironmentVariableW
0x101cd17c HeapAlloc
0x101cd180 SetFileInformationByHandle
0x101cd184 DuplicateHandle
0x101cd188 SetFilePointerEx
0x101cd18c GetProcessHeap
0x101cd190 GetStdHandle
0x101cd194 GetCurrentProcessId
0x101cd198 WriteFileEx
0x101cd19c SleepEx
0x101cd1a0 ReadFileEx
0x101cd1a4 TerminateProcess
0x101cd1a8 GetModuleHandleA
0x101cd1ac HeapFree
0x101cd1b0 HeapReAlloc
0x101cd1b4 WaitForSingleObjectEx
0x101cd1b8 lstrlenW
0x101cd1bc CreateMutexA
0x101cd1c0 CreateThread
0x101cd1c4 FindNextFileW
0x101cd1c8 FindClose
0x101cd1cc CreateFileW
0x101cd1d0 GetFileInformationByHandleEx
0x101cd1d4 CreateDirectoryW
0x101cd1d8 FindFirstFileW
0x101cd1dc DeleteFileW
0x101cd1e0 GetFinalPathNameByHandleW
0x101cd1e4 WideCharToMultiByte
0x101cd1e8 GetModuleHandleW
0x101cd1ec FormatMessageW
0x101cd1f0 GetModuleFileNameW
0x101cd1f4 CreateNamedPipeW
0x101cd1f8 GetFullPathNameW
0x101cd1fc GetSystemDirectoryW
0x101cd200 GetWindowsDirectoryW
0x101cd204 CreateProcessW
0x101cd208 GetFileAttributesW
0x101cd20c InitializeProcThreadAttributeList
0x101cd210 UpdateProcThreadAttribute
0x101cd214 MultiByteToWideChar
0x101cd218 WriteConsoleW
advapi32.dll
0x101cd02c SystemFunction036
0x101cd030 RegQueryValueExW
0x101cd034 RegCloseKey
0x101cd038 RegOpenKeyExW
ws2_32.dll
0x101cd268 send
0x101cd26c recv
0x101cd270 shutdown
0x101cd274 getsockopt
0x101cd278 setsockopt
0x101cd27c connect
0x101cd280 ind
0x101cd284 WSASocketW
0x101cd288 getsockname
0x101cd28c getpeername
0x101cd290 WSAGetLastError
0x101cd294 ioctlsocket
0x101cd298 closesocket
0x101cd29c WSAStartup
0x101cd2a0 WSACleanup
0x101cd2a4 WSAIoctl
0x101cd2a8 freeaddrinfo
0x101cd2ac getaddrinfo
0x101cd2b0 WSASend
secur32.dll
0x101cd23c DecryptMessage
0x101cd240 FreeCredentialsHandle
0x101cd244 ApplyControlToken
0x101cd248 FreeContextBuffer
0x101cd24c DeleteSecurityContext
0x101cd250 QueryContextAttributesW
0x101cd254 InitializeSecurityContextW
0x101cd258 AcquireCredentialsHandleA
0x101cd25c AcceptSecurityContext
0x101cd260 EncryptMessage
crypt32.dll
0x101cd09c CertDuplicateCertificateChain
0x101cd0a0 CertFreeCertificateChain
0x101cd0a4 CertCloseStore
0x101cd0a8 CertOpenStore
0x101cd0ac CertAddCertificateContextToStore
0x101cd0b0 CertEnumCertificatesInStore
0x101cd0b4 CertDuplicateStore
0x101cd0b8 CertGetCertificateChain
0x101cd0bc CertVerifyCertificateChainPolicy
0x101cd0c0 CertDuplicateCertificateContext
0x101cd0c4 CertFreeCertificateContext
ntdll.dll
0x101cd220 NtReadFile
0x101cd224 NtCreateFile
0x101cd228 NtDeviceIoControlFile
0x101cd22c NtCancelIoFileEx
0x101cd230 RtlNtStatusToDosError
0x101cd234 NtWriteFile
crypt.dll
0x101cd08c BCryptGenRandom
VCRUNTIME140.dll
0x101cd008 _except_handler4_common
0x101cd00c memcpy
0x101cd010 __CxxFrameHandler3
0x101cd014 memset
0x101cd018 memmove
0x101cd01c memcmp
0x101cd020 _CxxThrowException
0x101cd024 __std_type_info_destroy_list
api-ms-win-crt-heap-l1-1-0.dll
0x101cd050 malloc
0x101cd054 free
api-ms-win-crt-stdio-l1-1-0.dll
0x101cd080 __acrt_iob_func
0x101cd084 fgetc
api-ms-win-crt-runtime-l1-1-0.dll
0x101cd05c _cexit
0x101cd060 _initterm
0x101cd064 _initterm_e
0x101cd068 _seh_filter_dll
0x101cd06c _configure_narrow_argv
0x101cd070 _initialize_narrow_environment
0x101cd074 _initialize_onexit_table
0x101cd078 _execute_onexit_table
EAT(Export Address Table) Library
0x100027e0 DllMain
0x1001d320 bz_internal_error
0x10005300 g2mcomm_winmain
USER32.dll
0x101cd000 ShowWindow
api-ms-win-core-synch-l1-2-0.dll
0x101cd040 WaitOnAddress
0x101cd044 WakeByAddressAll
0x101cd048 WakeByAddressSingle
cryptprimitives.dll
0x101cd094 ProcessPrng
kernel32.dll
0x101cd0cc QueryPerformanceFrequency
0x101cd0d0 UnhandledExceptionFilter
0x101cd0d4 SetHandleInformation
0x101cd0d8 SetUnhandledExceptionFilter
0x101cd0dc IsProcessorFeaturePresent
0x101cd0e0 GetCurrentThreadId
0x101cd0e4 InitializeSListHead
0x101cd0e8 GetFileInformationByHandle
0x101cd0ec GetConsoleWindow
0x101cd0f0 GetProcAddress
0x101cd0f4 LoadLibraryA
0x101cd0f8 CloseHandle
0x101cd0fc GetConsoleMode
0x101cd100 IsDebuggerPresent
0x101cd104 CreateIoCompletionPort
0x101cd108 GetQueuedCompletionStatusEx
0x101cd10c PostQueuedCompletionStatus
0x101cd110 SetFileCompletionNotificationModes
0x101cd114 QueryPerformanceCounter
0x101cd118 GetNativeSystemInfo
0x101cd11c VirtualQuery
0x101cd120 VirtualAlloc
0x101cd124 VirtualFree
0x101cd128 VirtualProtect
0x101cd12c GetSystemInfo
0x101cd130 CreateFileMappingW
0x101cd134 MapViewOfFile
0x101cd138 UnmapViewOfFile
0x101cd13c GetSystemTimeAsFileTime
0x101cd140 FreeEnvironmentStringsW
0x101cd144 DeleteProcThreadAttributeList
0x101cd148 CompareStringOrdinal
0x101cd14c GetLastError
0x101cd150 SetThreadStackGuarantee
0x101cd154 GetCurrentThread
0x101cd158 SwitchToThread
0x101cd15c WaitForSingleObject
0x101cd160 GetCurrentProcess
0x101cd164 RtlCaptureContext
0x101cd168 ReleaseMutex
0x101cd16c SetLastError
0x101cd170 GetCurrentDirectoryW
0x101cd174 GetEnvironmentStringsW
0x101cd178 GetEnvironmentVariableW
0x101cd17c HeapAlloc
0x101cd180 SetFileInformationByHandle
0x101cd184 DuplicateHandle
0x101cd188 SetFilePointerEx
0x101cd18c GetProcessHeap
0x101cd190 GetStdHandle
0x101cd194 GetCurrentProcessId
0x101cd198 WriteFileEx
0x101cd19c SleepEx
0x101cd1a0 ReadFileEx
0x101cd1a4 TerminateProcess
0x101cd1a8 GetModuleHandleA
0x101cd1ac HeapFree
0x101cd1b0 HeapReAlloc
0x101cd1b4 WaitForSingleObjectEx
0x101cd1b8 lstrlenW
0x101cd1bc CreateMutexA
0x101cd1c0 CreateThread
0x101cd1c4 FindNextFileW
0x101cd1c8 FindClose
0x101cd1cc CreateFileW
0x101cd1d0 GetFileInformationByHandleEx
0x101cd1d4 CreateDirectoryW
0x101cd1d8 FindFirstFileW
0x101cd1dc DeleteFileW
0x101cd1e0 GetFinalPathNameByHandleW
0x101cd1e4 WideCharToMultiByte
0x101cd1e8 GetModuleHandleW
0x101cd1ec FormatMessageW
0x101cd1f0 GetModuleFileNameW
0x101cd1f4 CreateNamedPipeW
0x101cd1f8 GetFullPathNameW
0x101cd1fc GetSystemDirectoryW
0x101cd200 GetWindowsDirectoryW
0x101cd204 CreateProcessW
0x101cd208 GetFileAttributesW
0x101cd20c InitializeProcThreadAttributeList
0x101cd210 UpdateProcThreadAttribute
0x101cd214 MultiByteToWideChar
0x101cd218 WriteConsoleW
advapi32.dll
0x101cd02c SystemFunction036
0x101cd030 RegQueryValueExW
0x101cd034 RegCloseKey
0x101cd038 RegOpenKeyExW
ws2_32.dll
0x101cd268 send
0x101cd26c recv
0x101cd270 shutdown
0x101cd274 getsockopt
0x101cd278 setsockopt
0x101cd27c connect
0x101cd280 ind
0x101cd284 WSASocketW
0x101cd288 getsockname
0x101cd28c getpeername
0x101cd290 WSAGetLastError
0x101cd294 ioctlsocket
0x101cd298 closesocket
0x101cd29c WSAStartup
0x101cd2a0 WSACleanup
0x101cd2a4 WSAIoctl
0x101cd2a8 freeaddrinfo
0x101cd2ac getaddrinfo
0x101cd2b0 WSASend
secur32.dll
0x101cd23c DecryptMessage
0x101cd240 FreeCredentialsHandle
0x101cd244 ApplyControlToken
0x101cd248 FreeContextBuffer
0x101cd24c DeleteSecurityContext
0x101cd250 QueryContextAttributesW
0x101cd254 InitializeSecurityContextW
0x101cd258 AcquireCredentialsHandleA
0x101cd25c AcceptSecurityContext
0x101cd260 EncryptMessage
crypt32.dll
0x101cd09c CertDuplicateCertificateChain
0x101cd0a0 CertFreeCertificateChain
0x101cd0a4 CertCloseStore
0x101cd0a8 CertOpenStore
0x101cd0ac CertAddCertificateContextToStore
0x101cd0b0 CertEnumCertificatesInStore
0x101cd0b4 CertDuplicateStore
0x101cd0b8 CertGetCertificateChain
0x101cd0bc CertVerifyCertificateChainPolicy
0x101cd0c0 CertDuplicateCertificateContext
0x101cd0c4 CertFreeCertificateContext
ntdll.dll
0x101cd220 NtReadFile
0x101cd224 NtCreateFile
0x101cd228 NtDeviceIoControlFile
0x101cd22c NtCancelIoFileEx
0x101cd230 RtlNtStatusToDosError
0x101cd234 NtWriteFile
crypt.dll
0x101cd08c BCryptGenRandom
VCRUNTIME140.dll
0x101cd008 _except_handler4_common
0x101cd00c memcpy
0x101cd010 __CxxFrameHandler3
0x101cd014 memset
0x101cd018 memmove
0x101cd01c memcmp
0x101cd020 _CxxThrowException
0x101cd024 __std_type_info_destroy_list
api-ms-win-crt-heap-l1-1-0.dll
0x101cd050 malloc
0x101cd054 free
api-ms-win-crt-stdio-l1-1-0.dll
0x101cd080 __acrt_iob_func
0x101cd084 fgetc
api-ms-win-crt-runtime-l1-1-0.dll
0x101cd05c _cexit
0x101cd060 _initterm
0x101cd064 _initterm_e
0x101cd068 _seh_filter_dll
0x101cd06c _configure_narrow_argv
0x101cd070 _initialize_narrow_environment
0x101cd074 _initialize_onexit_table
0x101cd078 _execute_onexit_table
EAT(Export Address Table) Library
0x100027e0 DllMain
0x1001d320 bz_internal_error
0x10005300 g2mcomm_winmain