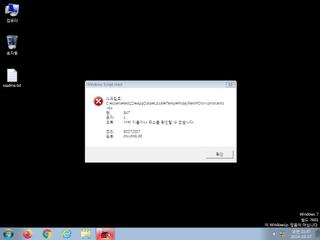
ScreenShot
| Created | 2024.10.27 11:53 | Machine | s1_win7_x6401 |
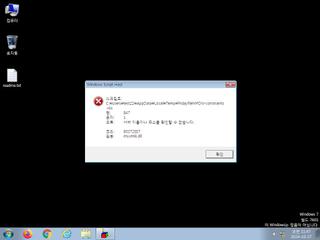
| Filename | fridayfileMPDW-constraints.vbs | ||
| Type | Little-endian UTF-16 Unicode text, with CRLF, CR line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | |||
| VT API (file) | 5 detected (gen40, SAgent, hrpyor) | ||
| md5 | 92361fe6feb25c67dae9dfefee911404 | ||
| sha256 | 16dfc05a6ccd93a5d80cb362553f196b5943b65db5028cb408e8d0e68f30c827 | ||
| ssdeep | 1536:bUJW4WzNe/PJe+vkery+bGNccc3gt5pzQUGwg:zS7rgt5pVGwg | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (1cnts)
| Level | Description |
|---|---|
| notice | File has been identified by 5 AntiVirus engines on VirusTotal as malicious |
Rules (0cnts)
| Level | Name | Description | Collection |
|---|